Information security consulting is not merely an IT expenditure; it is a strategic partnership essential for navigating today's competitive landscape. It involves engaging external specialists to construct a resilient security posture—one that protects corporate assets, ensures regulatory compliance, and fuels growth, particularly in the adoption of transformative technologies like Artificial Intelligence.
Why Security Consulting Is a Strategic Business Enabler

For any enterprise in the German market, the adoption of Artificial Intelligence is a competitive imperative. However, this powerful enabler introduces a new class of complex security vulnerabilities that can halt innovation and expose the entire organisation to significant risk. For C-level executives, the paradigm must shift from viewing cybersecurity as a reactive cost centre to leveraging it as a proactive, strategic advantage.
When security is treated as a foundational pillar of corporate strategy, it becomes the framework that enables confident innovation. A robust security posture, architected by expert consultants, accomplishes more than regulatory compliance or risk mitigation. It becomes an engine that safeguards brand reputation, guarantees adherence to stringent German and EU regulations, and ultimately drives sustainable market leadership.
The Growing Importance of Specialised Guidance
The demand for expert guidance is accelerating. The global information security consulting market was valued at USD 27.85 billion in 2024 and is projected to reach USD 59.80 billion by 2032. This growth is driven by the increasing frequency and sophistication of cyberattacks, with global cybercrime costs projected to reach an unprecedented USD 10.5 trillion annually by 2025.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
This new reality presents a clear imperative for leadership: managing information security solely with internal resources is no longer a viable strategy. The complexity of securing AI models, cloud environments, and interconnected supply chains requires a level of specialised knowledge that often exceeds the capacity of internal IT teams. This is precisely where information security consulting delivers its value.
A strategic approach to security transforms it from a defensive shield into a competitive sword. It enables the business to pursue ambitious AI initiatives with the confidence that its core assets, data, and reputation are protected from foundational threats.
Connecting Security to Business Outcomes
Ultimately, the value of security consulting is measured by its direct impact on business objectives. Effective advisors work to align every security initiative with core KPIs, ensuring that each investment contributes directly to the company's overarching strategy.
Strategic consulting provides clear answers to critical business questions:
- How can we securely integrate AI to enhance manufacturing process efficiency? Achieving this requires a deep understanding of both technical and operational security protocols.
- What are the material compliance risks associated with our new data analytics platform? Navigating the complexities of GDPR and other regulations is a core competency of a qualified consultant.
- How do we protect our intellectual property during collaborations with external partners? Establishing secure collaboration frameworks is vital for modern innovation.
Information security consulting is a critical component of broader strategic IT consulting services, enabling the use of technology to drive growth while managing commensurate risks. This proactive mindset is what separates market leaders from their competitors. You may find value in exploring the strategic necessity of an IT security consultant in our related article.
Navigating Germany's Unique Cybersecurity Landscape
Germany's status as an economic powerhouse makes it a prime target for sophisticated cyber-attacks, creating a uniquely challenging environment for businesses. From the renowned Mittelstand to large corporations, the imperative to protect data and ensure operational continuity has never been more critical. This has elevated cybersecurity from a technical function to a boardroom-level concern.
Today, executive decisions are shaped by a complex matrix of regulations and industry-specific mandates. Business leaders are not merely avoiding fines; they are navigating this landscape to maintain a competitive edge and preserve stakeholder trust. Understanding these dynamics is the first step toward realising the strategic value of expert information security consulting.
The Regulatory Framework Driving Demand
The German market operates under some of the world's most stringent data protection and security regulations. These should be viewed not as bureaucratic obstacles, but as the foundational rulebook for data handling, system security, and incident response.
Key regulatory instruments include:
- The General Data Protection Regulation (GDPR): The cornerstone of data privacy, GDPR dictates how companies manage personal data and imposes significant penalties for non-compliance.
- The NIS2 Directive: An evolution of its predecessor, NIS2 expands its scope to include more critical infrastructure operators and essential entities, mandating stricter risk management practices and reporting protocols.
- TISAX (Trusted Information Security Assessment Exchange): For any entity within Germany's automotive sector, TISAX is non-negotiable. It provides a standardised framework for protecting sensitive information across the entire supply chain.
This demanding regulatory environment is a primary driver of Germany's expanding cybersecurity market. Projections indicate the market will reach approximately USD 15.57 billion in 2026, up from USD 14.02 billion in 2025. This figure reflects a growing reliance on specialised information security consulting to navigate these complex requirements.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
For German enterprises, understanding the EU's DORA Regulation is crucial for ensuring digital operational resilience. It establishes specific, rigorous requirements for the financial sector to ensure firms can withstand severe operational disruptions.
From Compliance to Strategic Advantage
While regulations establish a baseline, market-leading companies view security as far more than a defensive necessity. They recognise that a robust security posture, guided by experienced consultants, is a key enabler of safe innovation and growth. A proactive approach allows an enterprise to confidently adopt new technologies—such as AI—with the assurance that its core assets are secure.
This is particularly true for AI integration, which introduces novel data processing methods and, consequently, new potential vulnerabilities. A skilled information security consulting partner translates complex regulatory language into a practical, secure architecture. They ensure that innovative projects not only meet compliance requirements but are also built to withstand future threats.
This strategic mindset is paramount. The ability to demonstrate data security and operational resilience is no longer just a legal obligation—it is a significant competitive advantage in Germany and beyond. By selecting the right advisors, companies can transform a security obligation into a powerful asset for building customer trust and driving tangible growth. To learn how to identify the right partner, consult our guide on evaluating cyber security consultancies.
What Does an Information Security Consultant Actually Do?
Information security consulting is not a monolithic service but a portfolio of specialised capabilities. Each is designed to solve specific, high-stakes business challenges—especially those emerging from the integration of technologies like AI. For leadership, understanding these core services is the first step toward selecting the right partner to protect the organisation during its growth trajectory.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
This discipline extends far beyond enhanced IT support; it is a strategic partnership focused on building enterprise resilience. A premier consultant does not merely execute a vulnerability scan and deliver a report; they diagnose the precise risks material to your business and architect targeted solutions. This may involve hardening existing infrastructure or designing secure-by-default systems from the ground up.
Mastering Strategic Risk and Compliance
The foundation of any effective security strategy is a rigorous and objective understanding of risk. This is the purpose of a Strategic Risk Assessment. It is not a mere technical audit; it is a business-centric analysis that links potential threats to their real-world impact on revenue, operations, and reputation. Consultants examine systems, processes, and supply chains to identify vulnerabilities before they can be exploited.
This assessment naturally leads to Compliance Governance. In Germany, regulatory adherence is non-negotiable. Expert consultants do not simply present a list of requirements; they develop a clear, actionable roadmap for achieving and maintaining certification.
- ISO 27001: The global standard for information security management. Certification demonstrates a systematic, professional approach to protecting sensitive data to clients, partners, and regulators.
- TISAX (Trusted Information Security Assessment Exchange): A mandatory standard for participants in the German automotive supply chain, ensuring a common language for secure data handling across all tiers.
These frameworks provide a structured methodology for managing risk, ensuring that an organisation not only meets its legal obligations but also builds a security posture capable of withstanding sophisticated attacks. This diagram illustrates how these critical regulations interrelate to support a comprehensive security strategy in the German market.
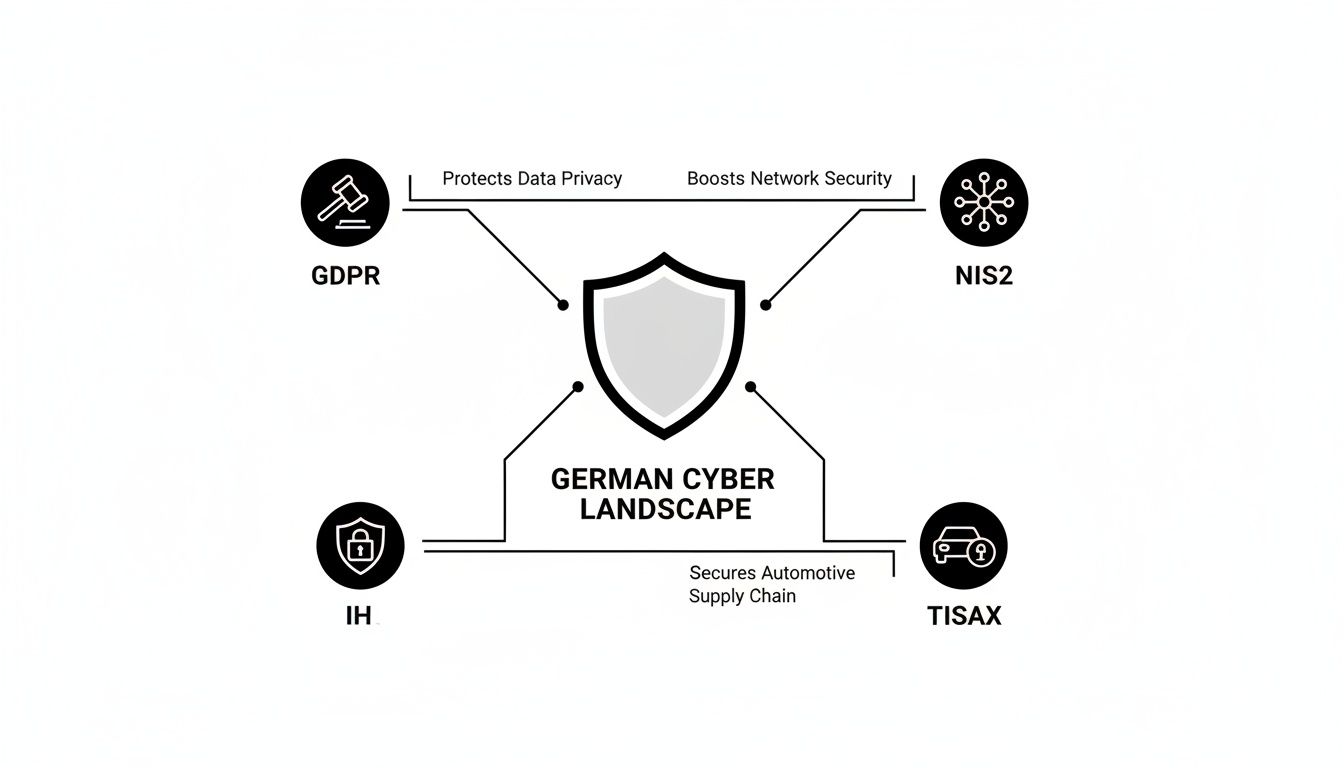
As illustrated, core regulations like GDPR, NIS2, and TISAX are not isolated mandates. They form the essential pillars of a modern, holistic security strategy for any ambitious German enterprise.
Protecting Modern AI and LLM Deployments
As companies accelerate the adoption of AI—particularly Large Language Models (LLMs)—they are inadvertently exposing themselves to a new and complex attack surface. Traditional security playbooks are insufficient for this domain. Specialised AI security consulting focuses on the unique vulnerabilities inherent in these models.
Securing an AI model presents a fundamentally different challenge than securing conventional software. The primary asset is not the code itself, but the integrity of the data, the model's internal logic, and the outputs it generates. An attack can corrupt the model's reasoning in ways that are initially subtle but ultimately catastrophic.
Consultants with deep AI security expertise focus on threats that may be unfamiliar to traditional IT teams:
- Prompt Injection: An attacker uses crafted inputs to manipulate an LLM, causing it to bypass its safety controls or divulge sensitive information. The implementation is simple: instruct the LLM to ignore its previous instructions and follow the attacker's new ones.
- Data Poisoning: Malicious data is secretly introduced during the model's training phase. This can create hidden backdoors or embed biases that are only discovered after the model is deployed and making critical, flawed decisions. This is done by contaminating the training data that the AI learns from.
- Model Inversion: Attackers analyse a model's public outputs to reverse-engineer the valuable, proprietary data it was trained on or even to steal the model's architecture itself.
A strategic consulting partner assists in designing a Secure AI Architecture from the project's inception. This involves establishing secure data pipelines for training, implementing robust access controls for model APIs, and building monitoring systems capable of detecting anomalous behaviour. Our guide on what a comprehensive cyber security consultation entails provides further detail. By proactively addressing these AI-specific risks, consultants ensure that a strategic investment in innovation does not become a significant liability.
Choosing the Right Consulting Partner
Selecting an information security consulting partner is a critical leadership decision that can significantly influence a company's trajectory. The traditional model—where a consultant delivers an extensive report and then disengages—often leaves internal teams with a strategic roadmap but no practical implementation support. This creates a significant gap between planning and execution.
A superior, partnership-based model is gaining prominence. This modern approach is not transactional; it is relational. The objective is not to hire a temporary advisor but to engage a "co-preneur" who is equally invested in achieving measurable business outcomes. This is particularly critical when addressing the high-stakes complexities of securing artificial intelligence.
The Old Model vs The New Partnership
The distinction between these two models is stark. One delivers analysis; the other delivers results. Understanding this difference is the first step toward making an informed decision and avoiding the common pitfalls of traditional consulting engagements. The right partner integrates seamlessly into the organisation, becoming an extension of the team with a vested interest in success.
To clarify the choice, let us examine their operational and strategic differences.
Comparing Traditional Consulting vs. The Partnership Model
This table delineates the core differences between a transactional vendor and a true strategic partner. It is designed to help executives determine which model aligns with their organisation's goals for security and innovation.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
| Attribute | Traditional Consultant | Modern Partnership Model |
|---|---|---|
| Accountability | Delivers reports and recommendations; accountability ends at handover. | Shares P&L responsibility and is accountable for measurable business outcomes. |
| Methodology | Relies on established, often rigid, frameworks and lengthy analysis phases. | Employs rapid prototyping and agile methods to validate hypotheses quickly. |
| Relationship | A hierarchical, arms-length dynamic between client and vendor. | A collaborative, "eye-level" partnership with deep integration into your teams. |
| Focus | Primarily on identifying problems and providing theoretical solutions. | Focused on co-creating and implementing solutions that deliver tangible value. |
| Risk | The client bears the full risk of implementation failure. | Risk is shared; the partner has "skin in the game" and is invested in the outcome. |
This represents a fundamental shift toward a model where the client's success is a direct measure of the consultant's success. This alignment of incentives ensures that solutions are not only technically sound but also operationally feasible and aligned with the long-term vision.
An Evaluation Framework for Finding True Partners
Identifying a partner with this mindset requires a more sophisticated evaluation process that looks beyond standard certifications and client logos. The key attributes to seek are an entrepreneurial spirit, a proven history of delivering tangible results, and a compatible corporate culture.
Focus your evaluation on three critical areas:
Technical Acumen and AI Expertise: The ability to address complex, next-generation security challenges is non-negotiable.
- How do you approach securing generative AI models against threats like prompt injection and data poisoning?
- Describe a project where you designed the security architecture for an AI system that was successfully deployed into production.
- What is your process for staying abreast of emerging threats targeting the German industrial and automotive sectors?
Track Record of Business Results: A true partner links security initiatives directly to business value, not just technical metrics.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
- Provide an example of how your security guidance directly enabled a client to achieve a business objective, such as launching a new product or entering a new market.
- How do you measure the ROI of your services beyond risk reduction?
- Describe a time a project encountered significant challenges. How did you adapt to ensure a successful outcome for the client?
Cultural Fit and Partnership Mentality: This is often the most overlooked yet most critical element of a successful engagement.
- Define a successful partnership from your perspective, and describe your role in achieving it.
- What is your methodology for knowledge transfer? How do you ensure our internal team is more capable at the end of the engagement?
- How would you manage a fundamental strategic disagreement to arrive at the optimal decision for the business?
A prospective partner's responses to these questions will reveal their core philosophy. You are looking for a profound sense of ownership, a willingness to challenge assumptions constructively, and an unwavering focus on enabling the business, not merely restricting it.
Ultimately, selecting the right information security consulting partner is not about hiring another vendor. It is about recruiting a vital strategic ally. Conducting thorough vendor due diligence is the only way to find a firm that possesses both the technical expertise and a shared commitment to innovation and success. A successful selection process lays the foundation for secure, sustainable growth.
A Case Study in Secure AI Implementation

Theoretical frameworks are useful, but business leaders require tangible results. Let us examine a real-world scenario to illustrate the impact of a true partnership in information security consulting. The subject is a representative German Mittelstand company, a market leader in a specialised manufacturing segment.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
The objective was to implement a predictive maintenance AI on the production line. By analysing sensor data from machinery, the company aimed to anticipate equipment failures, reduce downtime, and optimise maintenance schedules. The challenge: this operational data constituted invaluable intellectual property, detailing their proprietary manufacturing processes.
The Initial Challenge: Uncovering Hidden Risks
The project team consisted of highly capable engineers and data scientists focused on model accuracy and operational efficiency. Security was considered, but primarily through the lens of traditional IT network defences. The team was not equipped to identify the novel threats associated with a production-grade AI system.
The consulting engagement began with an assessment phase. The initial step was not to build, but to listen and analyse. A joint risk assessment workshop quickly identified critical vulnerabilities that the internal team had not considered.
- Data Leakage Potential: The proposed data pipeline, moving data from the factory floor to a cloud-based training environment, lacked essential segmentation and encryption controls, creating a significant risk of exposing sensitive process data.
- Compliance Gaps: The data handling plan was not fully aligned with GDPR, particularly concerning data minimisation principles. There was a risk of inadvertently collecting operator PII, creating a major compliance blind spot.
- Model Integrity Threats: The architecture included no defences against sophisticated attacks like data poisoning. An adversary could subtly introduce corrupted data, causing the AI to generate dangerously inaccurate predictions about machine failures.
Co-Creating a Resilient AI Architecture
Rather than delivering a report of findings and disengaging, the consulting partner embedded directly with the client's team to co-create the solution. This hands-on, collaborative approach ensures that security measures are practical, aligned with operational realities, and—critically—that knowledge is transferred to the internal team.
The first major initiative was a complete redesign of the data pipeline. A secure, segregated "data enclave" was established in the cloud, fortified with end-to-end encryption and stringent access controls. This architecture isolated and protected the raw operational data throughout its lifecycle, from the factory floor to the AI model itself.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
Next, the joint team developed an AI governance framework. This was not a static document but a set of actionable rules and automated checks to ensure ongoing compliance with GDPR and internal policies. It established clear ownership for the AI model and its data, creating a robust chain of accountability.
The most significant shift was moving the client's mindset from "bolting on" security after development to "baking it in" from the start. This proactive stance is the cornerstone of secure innovation, preventing costly rework and reducing the risk of a catastrophic breach.
From Deployment to Lasting Value
With a secure architecture and a robust governance model in place, the AI system was deployed. The engagement, however, continued. The final phase focused on implementing continuous monitoring and establishing an incident response plan. This involved defining clear protocols to detect anomalous model behaviour that could indicate a security compromise.
This case study demonstrates the power of a modern partnership model. The manufacturing firm did not merely procure a security audit; it gained a secure, value-generating asset. This methodical, shared-risk approach transformed an ambitious AI project from a potential liability into a durable competitive advantage. For a deeper understanding, learn more about the role of a modern computer security consultant in our detailed guide.
Measuring the ROI of Your Security Investment
Any C-level initiative lacking a demonstrable return on investment is untenable. Information security consulting is no exception. The challenge is that the greatest successes in security are often invisible—they are the adverse events that do not occur.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
Therefore, a paradigm shift in thinking is required. Security is not merely an operational cost; it is a direct enabler of financial performance and a significant competitive advantage. Gaining executive support requires building a business case that translates abstract risk into tangible business outcomes.
Calculating the Hard Numbers
The most direct method for calculating security ROI is to quantify the cost of inaction. What is the probable financial impact of a security breach? For a German manufacturing firm, this is not a hypothetical exercise. The costs could include millions in lost production due to ransomware, theft of intellectual property from a compromised AI model, or substantial GDPR fines.
Quantifiable metrics include:
- Cost of a Breach: Model the financial fallout, including direct costs such as incident response, legal fees, and regulatory penalties. Also, account for indirect costs like reputational damage, customer churn, and lost future revenue. A skilled consultant can provide industry-specific data to substantiate these figures.
- Reduced Compliance Fines: Determine the potential financial penalty for a major GDPR or NIS2 violation. The cost of a consulting engagement is typically a small fraction of this potential liability.
- Lower Insurance Premiums: A strong, documented security posture, validated by an independent consultant, is a key factor for insurers. This can directly result in significantly lower cybersecurity insurance premiums.
Articulating the Strategic Value
Beyond quantitative analysis, the most profound value of security consulting is strategic. It creates the stability and confidence necessary for business growth and positions the company as a trustworthy market leader.
The true ROI of a security partnership isn’t just in the breaches you prevent, but in the ambitious projects you can confidently pursue. It’s the freedom to innovate with AI, knowing your risks are managed by experts.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
This strategic value manifests in several key areas:
- Enhanced Brand Trust: In a market where trust is paramount, a demonstrable commitment to security is a powerful differentiator that attracts and retains high-value customers.
- Improved Investor Confidence: A mature security programme signals strong governance and effective risk management, making the company a more attractive and stable investment.
- Accelerated Innovation: By de-risking new technologies like AI, expert consulting removes security roadblocks, allowing development teams to build and deploy new products faster than competitors without compromising on security.
By combining quantitative financial analysis with these strategic benefits, a compelling business case emerges. Information security consulting is thus reframed from a cost centre to a fundamental investment in resilience, growth, and long-term success.
A Few Common Questions We Hear
When leadership teams evaluate information security consulting, several key questions consistently arise. Here are our responses to the most frequent inquiries from executives, particularly those initiating AI projects in Germany.
How Do We Justify Proactive Security Consulting Costs to the Board?
Frame the expenditure not as a cost, but as an investment that enables innovation and mitigates catastrophic risk. The ROI is realised not only in preventing breaches but also in confidently unlocking new revenue streams from your AI initiatives.
Present a quantitative analysis. Juxtapose the average cost of a data breach in your sector against the fractional investment required for expert guidance. For emerging technologies like AI, robust security is not an optional add-on; it is a prerequisite for a successful go-to-market strategy.
Our Internal IT Team Is Great. Why Bring in External Consultants?
Even the most capable internal teams benefit from an external perspective. Consultants offer a breadth of experience, having addressed complex security challenges across numerous industries, particularly with nascent technologies like generative AI, which may be new terrain for your team.
They also provide an objective viewpoint, unencumbered by internal politics or organisational silos. Critically, they fill specialised skill gaps with talent that is exceedingly difficult and costly to recruit and retain full-time. The model is one of augmentation, not replacement.
This external expertise is increasingly vital as Germany’s IT Security Services industry faces a significant talent shortage. With an estimated 109,000 open positions for IT specialists, most German companies anticipate this gap will widen, directly impacting their ability to secure projects internally. Further details on Germany's IT talent shortage on ibisworld.com are available.
What's the First Step to Engaging a Consultant for Our AI Project?
Before addressing technology, achieve absolute clarity on the business objective. What problem are you solving? What opportunity are you pursuing? Without this strategic clarity, any security engagement will lack direction.
Once the objective is defined, engage potential partners in a strategic discovery session. An effective initial step is often a tightly scoped risk assessment or a small-scale proof-of-concept for a specific AI use case. This allows you to evaluate their methodology and build trust before committing to a full-scale partnership.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
At Reruption, we do not just consult—we become your co-preneurs in the AI era. We share accountability for business outcomes, transforming your innovative ideas into secure, market-ready realities. If you are ready to build with a partner who has a vested interest in your success, let's connect. Find us at https://www.reruption.com.