A computer security consultant is a strategic partner tasked with designing and fortifying your enterprise's digital assets. This role has evolved beyond technical support into a critical business function, ensuring that innovation—particularly in emergent fields like Artificial Intelligence—does not introduce unacceptable levels of risk. Their mandate is to align the organisation's security posture with its primary strategic objectives.
Why a Consultant Is a Critical Business Partner
In the German market, the function of a computer security consultant has fundamentally shifted. It is no longer a reactive, technical role but a proactive, executive-level priority. Far from being a mere cost centre, this expert is a strategic business enabler who directly influences profitability, market positioning, and the secure adoption of new technologies. They bring an intrinsic sense of accountability for business outcomes, integrating security into the core fabric of corporate strategy.
An elite security consultant acts as the principal architect for your company’s digital future. As your organisation undertakes ambitious initiatives such as AI-driven automation or new data platforms, the consultant designs the underlying security blueprint. This foundational work ensures that your most valuable projects are built on a solid, resilient framework, not on latent vulnerabilities that could precipitate a catastrophic failure.
Bridging Innovation and Risk
The primary function of a modern consultant is to reconcile ambitious technological goals with the complex realities of cyber risk. German companies are innovating at an unprecedented pace, but each new system or AI model introduces potential attack vectors. A strategic consultant ensures that the pursuit of a competitive advantage does not inadvertently expose the enterprise to threats that could cripple operations or irrevocably damage its reputation.
Their core activities include:
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
- Strategic Risk Assessment: Evaluating how new technologies alter the organisation's overall business risk profile.
- Secure Architecture Design: Engineering resilient frameworks for high-stakes projects, such as secure AI and LLM deployment.
- Proactive Threat Modelling: Adopting an adversarial mindset to anticipate how new innovations might be targeted before they are launched.
A computer security consultant’s value is measured not only by the attacks they prevent, but by the innovations they securely enable. They transform security from a perceived impediment into a catalyst for confident, sustainable growth.
This strategic partnership is vital. In the same way a business intelligence consultant provides data-driven insights to guide executive decisions, a security consultant delivers risk-based intelligence to protect them. You can explore further how specialised consultants shape business outcomes in our analysis of business intelligence experts.
Ultimately, engaging a top-tier computer security consultant is an investment in your company’s future resilience. It provides the strategic foresight required to navigate an increasingly perilous threat landscape, empowering your teams to innovate boldly and securely. It is about converting potential liabilities into fortified competitive advantages.
Understanding the Modern German Threat Landscape
To appreciate why a specialist computer security consultant is no longer a discretionary expense, one must first comprehend the escalating threats confronting German enterprises. The operational paradigm has changed. We are no longer addressing generic viruses or indiscriminate hacking attempts.
Today’s reality involves organised, well-funded adversaries who operate with the sophistication of multinational corporations. They maintain R&D departments, offer customer support for their malicious toolsets, and execute attacks with cold, strategic precision.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
This new class of threat is designed to impact core business functions: your operations, your supply chain, and the very technology that underpins your competitive edge. From manufacturing facilities to automotive R&D centres, no sector is immune.
The Rise of Industrial-Scale Cybercrime
The most significant shift has been the professionalisation of cybercrime. In Germany, this trend is particularly evident. Ransomware-as-a-Service (RaaS) platforms now enable a broad spectrum of actors to lease powerful extortion tools, leading to a dramatic increase in attacks against the Mittelstand.
These are not simple data-encryption incidents. They are sophisticated, multi-stage campaigns. Adversaries first exfiltrate sensitive data, then encrypt critical systems. Finally, they threaten public disclosure of the stolen information, directly contacting your customers and partners. The resulting financial and reputational damage can be catastrophic.
Simultaneously, the digitisation of industrial environments—our operational technology (OT) and industrial control systems (ICS)—has created a dangerous new attack surface. As these systems are connected to corporate networks, they create direct pathways for criminals to halt manufacturing, sabotage processes, or even cause physical harm.
The metrics below do not merely quantify defensive needs; they illustrate how elevating security to a strategic priority directly enhances profitability, market position, and the confidence to innovate.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
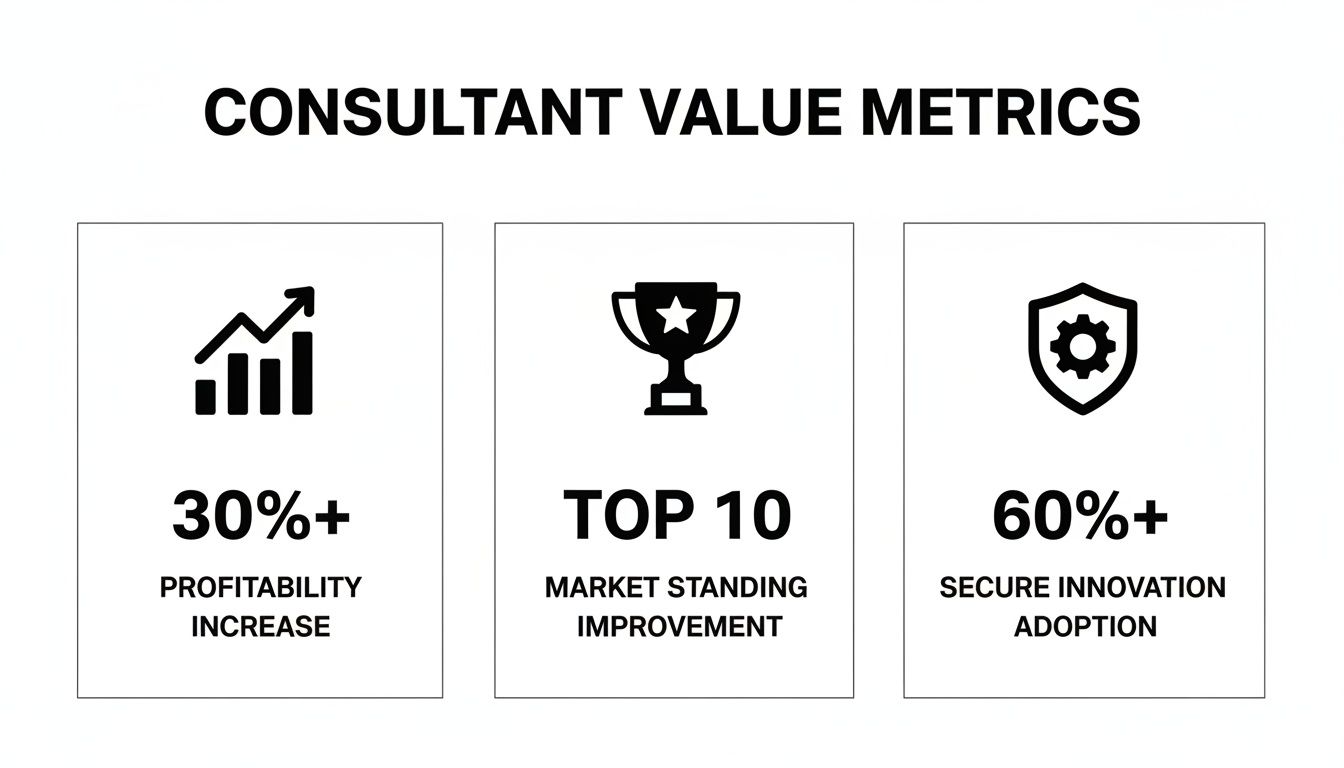
This data makes it clear: expert guidance is not a cost centre. It is an investment that builds tangible corporate value and enables forward progress without hesitation.
The following table summarises the most pressing threats currently facing German businesses.
Key Threat Metrics Facing German Enterprises
| Threat Vector | Key Statistic | Business Implication |
|---|---|---|
| Malware Proliferation | 309,000 new variants identified daily by the BSI | Constant pressure on detection systems, requiring adaptive and predictive defences beyond standard antivirus. |
| Ransomware Attacks | A primary and growing threat to German enterprises | Potential for complete operational shutdown, massive financial extortion, and severe reputational harm. |
| Software Vulnerabilities | Nearly 70 new vulnerabilities exploited by attackers every day | A relentless pace that makes timely patching a significant challenge, creating windows of opportunity for attackers. |
| Supply Chain Attacks | Targeting smaller partners to infiltrate larger organisations | Your security is only as strong as your weakest link; a partner's breach can become your own crisis. |
These figures present a stark reality: the volume and velocity of modern attacks can easily overwhelm even well-resourced internal IT teams.
AI as a New Attack Vector
Generative AI introduces another layer of complexity. While a powerful tool for innovation, it is also a formidable weapon for adversaries. AI is now used to craft flawless, highly persuasive phishing emails in perfect German, generate malware that dynamically alters its signature to evade detection, and even clone a CEO's voice to authorise fraudulent wire transfers.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
The only viable response is to counter AI-driven attacks with an equally sophisticated, AI-driven defence strategy—a capability beyond the reach of most in-house teams.
The data confirms this trend. Germany’s cybersecurity situation deteriorated significantly in 2023-2024. The Federal Office for Information Security (BSI) registered a 26% increase in new malware variants compared to the previous year.
The modern threat is not a technical problem to be solved by an IT department. It is a strategic business risk that demands executive-level attention and specialised, forward-looking expertise.
Yesterday’s security playbook is obsolete. A computer security consultant provides the critical external perspective needed to navigate this new reality, helping you build a security posture that is truly resilient. To understand their specific functions in greater detail, our guide on the strategic roles of cyber security consultants is an excellent resource.
Core Services an Elite Consultant Delivers
Engaging a top-tier computer security consultant is not merely procuring a technical auditor; it is securing a strategic partner who assumes ownership of business outcomes. The distinction is critical. A standard auditor identifies problems; a true partner designs, validates, and helps implement solutions that advance the business.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
Consider this analogy: an auditor might identify a vulnerability in your new product pipeline, halting your launch. A partner-consultant, conversely, is engaged from the project's inception. They help design the secure data architecture, validate it against real-world threat models, and upskill your team for long-term management. Security transforms from a bottleneck into an accelerator for innovation.

Strategic Risk Assessment and Management
A high-calibre consultant's first action is to conduct a risk assessment directly linked to business objectives. This is not a standard IT checklist. It involves mapping your company’s unique threat surface—from supply chains to operational technology—to material impacts, such as potential financial and reputational damage.
This process involves:
- Threat Modelling for Innovation: Analysing how adversaries might exploit a new AI-driven automation system before it is deployed.
- Business Impact Analysis: Quantifying the potential cost of a breach in concrete terms—lost revenue, operational downtime, regulatory fines—to build a robust business case for security investments.
- Executive Risk Reporting: Translating complex technical risks into clear, concise language that enables decisive action by the C-suite and the board.
This strategic perspective ensures that your security budget is not allocated based on recent threat headlines but is instead laser-focused on protecting the bottom line.
Secure AI and LLM Deployment Architecture
For any executive focused on innovation, deploying Artificial Intelligence and Large Language Models (LLMs) is a top priority—as are the associated risks. An expert consultant provides the specialised architecture needed to leverage these powerful technologies without introducing catastrophic vulnerabilities.
A consultant’s value in this context is not to slow AI adoption with warnings, but to build the secure guardrails that enable you to accelerate it with confidence. They de-risk the very core of your future competitive advantage.
This is practical, hands-on work. They will design secure data pipelines for model training, implement controls to prevent threats like model poisoning or data leakage, and establish governance frameworks to ensure AI use remains ethical and responsible. This is what is required to transform an ambitious AI roadmap into a secure, production-ready reality. For a deeper understanding of these mechanics, review our article on how cyber security consultants operate.
Advanced Compliance and Certification Management
In the German market, compliance is not optional. Standards like TISAX for the automotive sector and ISO 27001 for information security are fundamental requirements for market participation. An elite consultant navigates these complex landscapes, transforming a perceived burden into a distinct market advantage.
Their role extends beyond audit preparation. A true partner embeds compliance requirements into daily operations, ensuring that security practices are sustainable. This proactive approach not only expedites certification but also builds trust within your supply chain and establishes a security posture that satisfies both auditors and customers.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
The services segment of Germany's cybersecurity market, driven by consulting, is projected to expand at a 10.7% CAGR through 2030. This growth is fuelled by a significant talent shortage and the pressing need for SMEs to achieve certification to remain competitive.
Integrating AI Security and Regulatory Compliance
For German enterprises, the integration of AI is a strategic imperative, not just a technological upgrade. This initiative, however, must be executed within one of the world's most stringent regulatory environments. Consequently, security and compliance can no longer be managed in separate silos; they must be unified into a single, cohesive strategy. This is precisely where a skilled computer security consultant provides critical value.
Successful AI deployment requires navigating a complex web of standards. For participants in the automotive supply chain, TISAX (Trusted Information Security Assessment Exchange) is a prerequisite. For most other industries, ISO 27001 serves as the foundational framework for information security management. A consultant's role is to leverage these regulations not as obstacles, but as blueprints for building AI systems that are resilient, trustworthy, and confer a competitive advantage.

From Compliance Burden to Competitive Edge
Certification is not the end goal; it is the mechanism through which superior AI systems are built. A consultant orchestrates this process, focusing on the unique vulnerabilities of AI systems and ensuring that every decision aligns with both security best practices and regulatory mandates. This proactive governance builds profound trust with partners, customers, and auditors.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
Consider the immediate value they deliver in these core areas:
- Governing AI Training Data: They establish strict protocols to ensure training data is sourced ethically, properly anonymised, and handled in accordance with GDPR. This is not merely good practice; it is essential for preventing catastrophic data privacy breaches.
- Securing AI Infrastructure: They design and harden the deployment environment—whether on-premises or cloud-based—to protect against model theft, data poisoning, and adversarial attacks that can manipulate AI-driven decisions.
- Documenting for Auditability: They create the meticulous documentation required by TISAX and ISO auditors, providing verifiable proof that security controls are not just planned, but are actively implemented, monitored, and maintained.
A Practical Case Study in Manufacturing
Consider a German manufacturing firm implementing an AI-powered predictive maintenance system. The objective is to anticipate machine failures on the production line and schedule repairs pre-emptively, preventing costly downtime. The system requires processing vast amounts of sensitive operational data. A computer security consultant is engaged to oversee security and compliance from the project's inception.
Their methodical approach would be as follows:
- Initial Assessment: They conduct a thorough data classification exercise based on ISO 27001 principles. As the firm is a key automotive supplier, they also map all applicable TISAX requirements.
- Secure Architecture: They design a fortified, segregated network for the AI model, ensuring the training data is isolated from the corporate network and the deployed model is protected from tampering.
- Process Integration: They collaborate with the engineering team to embed security checkpoints directly into the development lifecycle and provide training on secure data handling protocols. The result is a robust, audit-ready process designed for long-term sustainability.
By integrating compliance directly into the AI development lifecycle, the consultant transforms a regulatory requirement into a strategic asset. The certified system not only enhances operational efficiency but also solidifies the company's reputation within the highly competitive automotive supply chain.
As part of this process, evaluating emerging threats and solutions is critical. For instance, the use of machine learning fraud detection for internal risk is rapidly becoming a standard tool for proactively managing internal threats.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
Ultimately, this integrated approach ensures that innovation does not introduce new vulnerabilities. A skilled consultant demonstrates that meticulous compliance is not a barrier to progress but the very foundation upon which safe, effective, and market-leading AI solutions are built. To understand how this fits into a broader framework, our guide on holistic risk management and compliance provides valuable higher-level context.
How to Select Your Strategic Security Partner
Selecting the right computer security consultant is an executive-level decision, not a procurement task. The objective is to find a partner who aligns with your strategic vision, not merely an individual who possesses a list of technical certifications. For leaders in innovation and product development, the ideal partner thinks like a founder, takes ownership of outcomes, and strengthens your internal team—rather than creating long-term dependency.
The selection process is about identifying an expert who understands that security should be a business enabler, not an obstacle. The traditional consulting model is broken: a consultant identifies problems, delivers a voluminous report, and leaves your team to manage the complex implementation. A true partner embeds with your organisation, shares responsibility for the outcome, and focuses on building secure, resilient systems that accelerate your time-to-market.
This distinction is paramount, particularly given the acute talent shortage. Germany’s cybersecurity market is projected to reach USD 23.89 billion by 2030, yet the industry faces a shortfall of 96,300 IT security professionals. With universities supplying only 7% of the required talent, companies must seek external expertise. They require not just advice, but execution capability. You can find a complete analysis of Germany's booming cybersecurity market and its implications for leadership.
Differentiating a Consultant from a Partner
To make an informed decision, you must understand the fundamental difference between a typical consultant and a genuine strategic partner. This choice will directly impact your ability to innovate securely without sacrificing momentum. A side-by-side comparison reveals a significant gap in mindset and expected outcomes.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
The following matrix provides a framework for your evaluation, contrasting the two approaches across criteria that are critical to business success.
Consultant Evaluation Matrix
This is not merely a checklist, but a strategic tool for leadership to penetrate the noise and assess potential security advisors based on what truly drives business value.
| Evaluation Criterion | Traditional Consultant Approach | Strategic Partner Approach |
|---|---|---|
| Mindset & Focus | Audit-focused; identifies problems and delivers findings in a report. | Business-focused; co-develops solutions and shares accountability for results. |
| Engagement Model | Transactional; project-based with a defined, often rigid, scope. | Relational; collaborative and adaptive, focused on long-term capability building. |
| Team Interaction | Operates as an external auditor, creating a potential dependency. | Integrates with your team, prioritising knowledge transfer and enablement. |
| Success Metric | Delivery of a comprehensive report or audit finding. | Measurable business outcomes like accelerated time-to-market or de-risked innovation. |
Using such a framework shifts the conversation from "What are your certifications?" to "How will you contribute to our strategic success?" It ensures you identify a partner who is aligned with your core business objectives. For a deeper exploration of this methodology, our article on system engineering in IT offers relevant insights.
Incisive Questions for Your Top Candidates
Once you have a shortlist, the interview must probe beyond technical expertise to uncover business acumen and strategic thinking. Avoid generic questions that elicit rehearsed answers. Instead, present them with real-world challenges that your teams currently face.
The right partner will not provide a textbook answer. They will begin by asking clarifying questions about your business context, risk appetite, and strategic goals before proposing a solution.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
Incorporate questions like these into your interviews:
- On Balancing Priorities: "We are launching a new AI-powered product in six months. How would you advise us on balancing the imperative for speed with the non-negotiable security hardening required?"
- On Team Enablement: "Our engineering team is highly capable but lacks deep security expertise. What is your methodology for upskilling them to own and manage the solutions you help us implement?"
- On Business Impact: "Imagine you discover a critical vulnerability in our primary revenue-generating system one week before a major marketing launch. Walk me through how you would present the risk and your remediation plan to the board."
These questions are designed to foster a substantive discussion about trade-offs, communication, and business reality—the factors that distinguish a consultant from a partner. If your organisation is preparing for a SOC 2 audit, you will face similar high-stakes vendor decisions; this excellent guide to choosing SOC 2 audit firms details the importance of this strategic mindset.
Their responses will provide a direct window into their thought process, operational style, and whether they possess the strategic depth to be a true co-preneur on your innovation journey.
An Action Plan for Securing Future Innovation
Navigating the intersection of high-stakes innovation and sophisticated security threats requires more than a robust defence; it demands a clear, executive-led strategy. Recognising the need for a computer security consultant is the first step; engaging the right one is a critical business process that can determine the success of your next major initiative.
This action plan serves as a roadmap for leaders who must translate strategic intent into tangible results, ensuring that every investment in technology and AI fuels secure, sustainable growth. This is not a procurement checklist, but a guide to forging a true strategic partnership.
Step 1: Define Your Strategic Objectives
Before initiating contact with any potential partner, the first action is internal. Convene key stakeholders—product leaders, innovation managers, legal counsel, and operations executives—to establish a unified vision. What is the single most critical business outcome this engagement must deliver?
Your core objectives might include:
- Achieving Compliance Certification: Securing a TISAX or ISO 27001 certificate is necessary to win a major contract or solidify your position in a high-value supply chain.
- Securing a High-Stakes AI Application: The launch of a new AI platform must be protected against data poisoning, model theft, and other advanced threats.
- Upskilling Your Internal Teams: The objective is to move beyond dependency by engaging a partner who actively trains your engineers to manage security independently.
Unambiguous clarity at this stage is non-negotiable. A vaguely defined goal will yield a vague outcome. A sharp, well-defined objective serves as the guiding principle for the entire engagement, from partner selection to the measurement of success.
Step 2: Shortlist Partners with Strategic Acumen
With your objectives defined, the next step is to identify partners who possess both deep technical expertise and a practical understanding of your business. Revisit the evaluation framework discussed previously to differentiate between traditional auditors and genuine strategic partners. You are seeking a firm that thinks like a co-founder, prepared to share accountability for business outcomes.
The right partner will not begin the conversation by discussing tools or vulnerabilities. They will start by inquiring about your business model, growth targets, and risk appetite. Their primary objective is to understand your strategy, not just your servers.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
Focus your search on consultants with a proven track record in your industry. Identify candidates who can clearly articulate how they have enabled innovation, not merely how they have prevented incidents.
Step 3: Structure a Value-Driven Pilot Project
Finally, avoid committing to a large, open-ended contract. Instead, validate the partnership through a focused pilot project. Select a high-value, specific use case where a tangible result can be achieved quickly. This could involve securing a single AI model, conducting a penetration test on an upcoming product, or drafting a security roadmap for a specific business unit.
This approach offers several advantages:
- It provides a low-risk opportunity to evaluate the consultant's working style and cultural fit with your team.
- It delivers a quick win, building internal momentum and demonstrating an immediate return on investment.
- It establishes a foundation of trust and proven results, which is essential before committing to a long-term strategic partnership.
By following this deliberate plan, you transform the engagement of a computer security consultant from a reactive necessity into a proactive, strategic investment. It becomes a direct enabler for confident, secure, and sustainable growth in the age of AI.
Frequently Asked Questions
When considering the engagement of a computer security consultant, the primary questions invariably concern cost, timelines, and integration with internal teams. Below are direct answers to the most common inquiries from executive leadership in Germany.
What is the typical cost of an engagement in Germany?
A single price does not exist for a strategic security consultant in Germany. The cost is contingent upon the scope of work, the level of expertise required, and the desired business outcomes. For most medium to large enterprises, engagements are structured as either a project-based fee or a long-term retainer.
A discrete project, such as a TISAX readiness assessment or the secure architecture design for a new AI product, typically ranges from €20,000 to €80,000, depending on complexity and duration. For ongoing strategic advisory services, a monthly retainer between €5,000 and €15,000 is standard, based on the level of consultant involvement.
The most effective way to view the cost is as an investment, not an expense. The critical question is not "What is the cost?" but rather "What is the cost of inaction, or worse, of a security breach?"
Optimal engagement models link fees directly to the achievement of specific business objectives, ensuring that your investment generates measurable value.
What is the timeline for TISAX or ISO 27001 certification?
Achieving a major certification like TISAX or ISO 27001 is a significant undertaking, even with expert guidance. For a well-organised company of 500+ employees, a realistic timeline is six to twelve months from the initial gap analysis to the final, successful audit.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
A typical project timeline can be broken down as follows:
- Initial Assessment & Scoping (1-2 months): The consultant performs a deep analysis of your current Information Security Management System (ISMS) to define the precise scope of the certification.
- Remediation & Implementation (3-6 months): This is the most intensive phase. The consultant partners with your teams to close identified gaps, implement necessary controls, and prepare all required documentation.
- Internal Audit & Final Preparation (1-2 months): A pre-assessment audit is conducted to identify and resolve any remaining issues before the formal audit.
- External Audit & Certification (1-2 months): The final stage, where an accredited body conducts the formal audit.
The consultant acts as both project manager and subject matter expert, accelerating the process by preventing common errors and ensuring all requirements are met.
How can a consultant and our in-house team collaborate effectively?
Effective collaboration depends on viewing the consultant as a strategic ally, not an external critic. The objective is to augment your team's capabilities, not to replace them. This is best achieved by establishing clear roles and a shared objective from the outset.
The consultant should lead high-level strategy, complex architectural design, and specialised compliance tasks where an external perspective provides maximum value. Your in-house team, with their deep knowledge of your systems, should own the daily implementation and management of security controls.
This model creates a powerful dynamic. Your team gains new skills through knowledge transfer from the consultant, reducing long-term dependency on external expertise. The consultant functions as a mentor, empowering your personnel to maintain a stronger, more resilient security posture long after the engagement concludes.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
As Reruption GmbH, we act as Co-Preneurs for the AI Era, partnering with you to turn ambitious ideas into secure, market-leading innovations. Learn more about our approach at https://www.reruption.com.