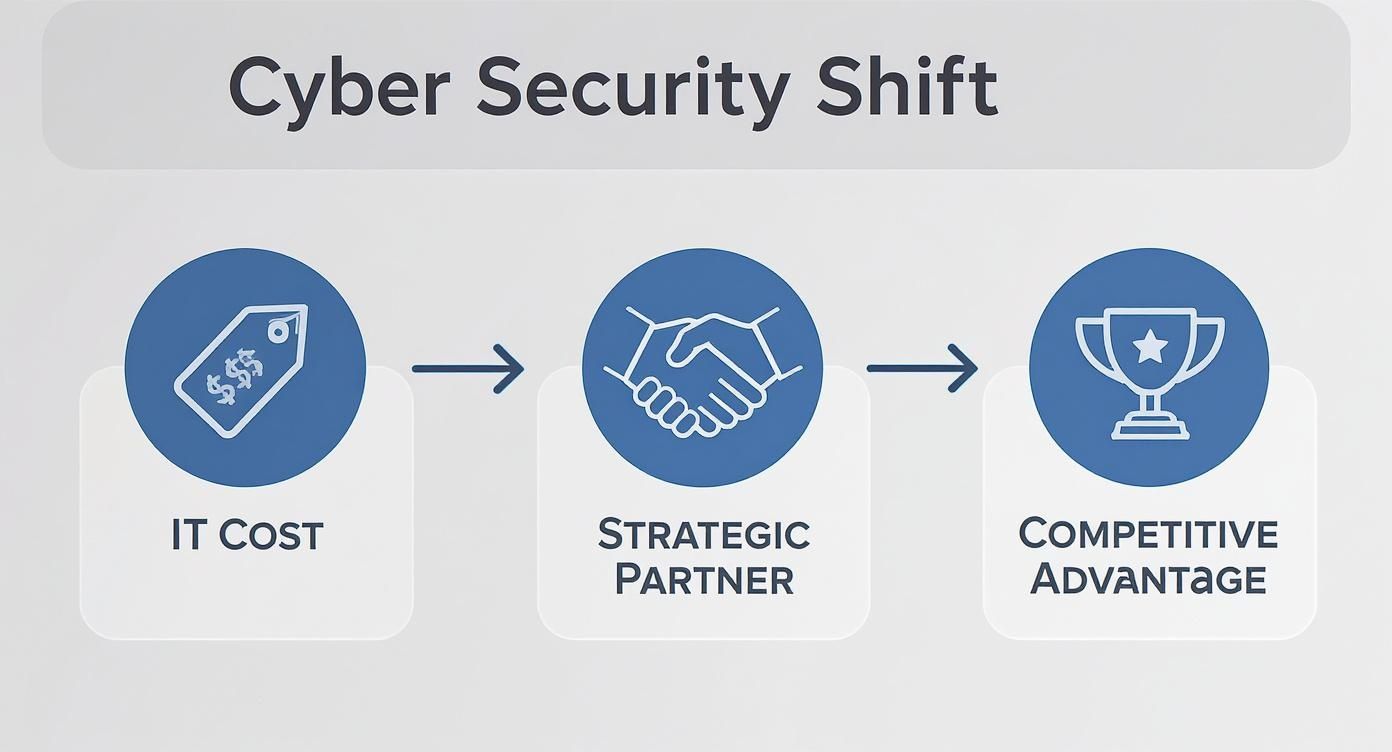
A cyber security consultancy is no longer a mere external IT function; it is a strategic advisor enabling your enterprise to navigate the complexities of digital protection, risk management, and an increasingly stringent regulatory environment. For C-level leadership focused on innovation, this paradigm shift elevates cyber security from a technical issue to a core component of business strategy.
Why Security Is Now a C-Suite Imperative

Historically, cyber security was confined to the IT department—a necessary budget line item, yet seldom a topic of boardroom discussion. This is no longer the case. The conversation has migrated from the server room to the C-suite, transforming security from a technical checkbox into an integral element of corporate strategy and innovation.
Two primary forces are compelling this evolution. First, the proliferation of Artificial Intelligence (AI) has equipped adversaries with a new arsenal of sophisticated tools capable of circumventing legacy defences. These AI-driven threats necessitate an equally intelligent and strategic response. Second, regulatory authorities across Germany and the European Union are intensifying oversight, placing direct accountability upon executive leadership.
The New Regulatory Landscape
New frameworks such as NIS2 and the Digital Operational Resilience Act (DORA) are not merely IT guidelines; they are direct mandates for the board. These regulations stipulate that companies must proactively manage risk and demonstrate operational resilience. Non-compliance results in significant financial penalties and, more damagingly, a reputational impact that can erode market trust instantaneously.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
This new reality requires a fundamental shift in perspective. Cyber security is no longer solely about preventing adverse events; it is about enabling positive outcomes.
A robust security posture is a competitive advantage. It provides the organisation with the confidence to embrace emerging technologies like AI, de-risk innovation, and cultivate trust with customers and partners in an increasingly volatile global environment.
From Vendor to Strategic Partner
This is precisely where the value of premier cyber security consultancies becomes evident. Selecting a consultancy is not a simple procurement exercise; it is the formation of a strategic partnership with a ‘co-preneur’—an entity that understands your business objectives and integrates resilience directly into your growth strategy.
A critical aspect of this leadership role involves effectively communicating cyber risk to boards and executives. The right partner translates technical complexities into clear business implications, empowering leadership to make informed, strategic decisions. They enable you to innovate securely, transforming security from a defensive measure into a potent engine for long-term corporate success.
Understanding the German Cybersecurity Market

Within Germany, the strategic landscape is evolving. Cybersecurity is no longer relegated to the IT budget; it is a central topic of boardroom deliberation. This shift is not driven by fear, but by a new reality defined by significant financial risk and stringent legislation that holds the C-suite directly accountable.
The economic data presents a compelling narrative. The German cybersecurity market is experiencing substantial growth, a direct response to both tangible threats and a more demanding legal framework.
The German market is projected to reach USD 15,102.7 million in revenue in 2025 and is forecasted to grow to USD 33,397.6 million by 2033. This surge is underpinned by a significant increase in corporate spending, with firms now allocating 18% of their IT budgets to security—a twofold increase from the 9% allocated in 2022. A detailed German market analysis provides further insights into these trends.
This is not discretionary spending. With cyberattacks inflicting over EUR 202.5 billion in damages annually, it is understandable why nearly 60% of German companies now perceive these incidents as an existential threat.
Regulatory Pressure Creates Board-Level Accountability
Beyond financial implications, a wave of EU and German legislation has formally established security as a board-level responsibility. These are not technical recommendations but legal frameworks that make leadership personally accountable for organisational resilience.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
Two key legislative acts are driving this transformation:
- The NIS2-aligned BSI Act (BSIG): This legislation expanded the number of regulated entities in Germany from approximately 4,500 to nearly 29,000. It imposes strict deadlines for incident reporting and rigorous security standards, enforced by substantial penalties for non-compliance.
- The Digital Operational Resilience Act (DORA): Targeted at the financial sector, DORA establishes a comprehensive framework for managing ICT risk. It mandates robust testing, diligent third-party vendor management, and strict incident reporting to ensure the stability of the EU's financial system.
In essence, these laws render resilience a legal obligation. Organisations can no longer afford a reactive posture; they must embed security into their foundational strategy.
The Strategic Imperative for Expert Guidance
The convergence of escalating financial risks and a complex regulatory environment creates a high-stakes climate where inaction is the most perilous course. Navigating this landscape requires a level of specialised expertise that most organisations do not possess internally.
Engaging expert cyber security consultancies thus becomes a strategic imperative. These partners provide the critical knowledge required to interpret regulations, implement appropriate controls, and develop a security posture that enables, rather than hinders, business objectives.
This proactive investment transcends mere defence. It is a fundamental component of modern corporate governance and a cornerstone for any enterprise aiming for sustainable, long-term growth.
Evaluating Core Services and Engagement Models

Engaging a cyber security consultancy is not merely a service procurement; it is an investment in strategic value. A clear understanding of the capabilities offered is essential. Modern consultancies provide a spectrum of services, and aligning these with your corporate objectives is the foundational step toward a successful partnership.
A robust security posture is analogous to a high-performance system, comprising several interconnected disciplines, each playing a critical role.
Key Service Pillars of Modern Consultancies
While service catalogues may be extensive, most offerings are built upon three core pillars that address the intersection of technology, risk, and compliance. Understanding the specific roles and services of cyber security consultants provides a valuable baseline for expectations.
- AI Security and Compliance: This extends far beyond application vulnerability testing. It involves securing the entire AI lifecycle—from data ingestion and model training to deployment and continuous monitoring. The objective is to ensure AI innovations are resilient against adversarial manipulation and compliant with emerging regulations such as the EU AI Act.
- Threat Intelligence: This functions as an early-warning system. Consultants analyse global threat data to identify risks pertinent to your specific industry and operational context. The focus is on proactive measures, enabling you to anticipate an attacker's strategy rather than reacting to its consequences.
- Governance, Risk, and Compliance (GRC): GRC provides the strategic framework that unifies security efforts. It aligns security initiatives with business objectives, translates technical data into business impact, and ensures that security investments are both effective and justifiable to the board. It is the mechanism for managing standards like ISO 27001 or TISAX.
These pillars must function as an integrated system. Threat intelligence should inform risk assessments, and AI security measures must be governed by the established GRC framework.
Engagement Model Comparison for Strategic Cybersecurity Partnership
The structure of your relationship with a consultancy is as critical as the services delivered. The selected model should align with your internal capabilities, corporate ambitions, and desired level of collaboration. The market presents two primary engagement models, leading to distinct outcomes and ownership structures.
The following table delineates the key differences between a traditional, project-based model and a more integrated, co-preneurial partnership.
| Attribute | Traditional Consultant Model | Co-preneur Partnership Model (e.g., Reruption) |
|---|---|---|
| Mindset | Vendor-Client: Transactional, focused on delivering a defined project or report. | Shared-Ownership: Collaborative, focused on achieving mutual business outcomes and shared success. |
| Accountability | Deliverable-Based: Accountable for completing the task (e.g., the audit report). | Outcome-Based: Jointly accountable for the business impact (e.g., reduced risk, successful product launch). |
| Scope | Tactical & Fixed: Addresses a specific, isolated problem like a penetration test or a policy review. | Strategic & Evolving: Addresses the entire security lifecycle and adapts to changing business needs. |
| Duration | Short-Term: Project-based, ends upon completion of the deliverable. | Long-Term: Continuous engagement, designed to build lasting resilience and capability. |
| Integration | External Advisor: Operates outside the core team, providing recommendations. | Embedded Partner: Functions as an extension of your internal team, driving implementation. |
Ultimately, the choice of model reflects a fundamental strategic decision.
Are you procuring a one-time project with a discrete deliverable, or are you investing in a true partnership where both parties share accountability for success?
The answer determines whether your security function remains a reactive cost centre or evolves into a proactive driver of business growth. For discrete, well-defined problems, a project-based approach may suffice. However, to integrate security into the fabric of innovation and transform it into a competitive advantage, a long-term, integrated partnership is the superior strategic choice. An effective https://reruption.com/en/knowledge/blog/cyber-security-consultation should feel less like a transaction and more like a collaborative venture.
Solving the Cybersecurity Talent Shortage
A significant challenge facing German corporate leadership is not technological but human: a pronounced deficit between the demand for skilled cybersecurity professionals and the available talent pool. This has rendered a purely in-house security strategy unattainable for many large enterprises.
This is not merely a recruitment challenge but a structural issue with significant financial implications. The scarcity of specialised talent inflates acquisition and retention costs, diverting capital that could otherwise fuel innovation or core business growth. Building an elite internal security team from scratch has become prohibitively expensive and time-consuming.
The Scale of Germany's Talent Deficit
The data is unequivocal. Germany entered 2025 with 96,300 open IT security positions, a 25% increase year-over-year. However, the talent pipeline is insufficient to meet this demand. While 28 universities offer specialised cybersecurity degrees, they produce only approximately 3,400 graduates annually, satisfying a mere 7% of the open roles.
This imbalance has driven substantial salary growth. A senior SOC analyst in Munich, for instance, now commands an average salary of EUR 96,000—a 57% increase since 2019. These escalating salary costs are becoming a fixed burden on corporate budgets. The German cybersecurity market and its talent dynamics offer a comprehensive overview of this issue.
This reality compels executive boards to address a critical question: is building and maintaining an elite internal security team the most effective allocation of capital and corporate focus? For an increasing number of businesses, the answer is no.
Reframing the Shortage as a Strategic Opportunity
Partnering with a specialist cyber security consultancy transforms this challenge. It reframes the talent shortage from an operational impediment into a strategic advantage. Instead of engaging in a costly and protracted war for talent, you gain immediate access to a team of seasoned experts with diverse experience across multiple industries and complex scenarios.
This approach delivers distinct benefits:
- Immediate Access to Scarce Expertise: Bypass lengthy recruitment cycles and engage specialists in niche domains such as AI security, cloud compliance, or industry-specific threat intelligence.
- Reduced Overhead and Predictable Costs: Convert the unpredictable and escalating costs of salaries, benefits, and continuous training into a manageable, predictable operational expense.
- Focus on Core Business Objectives: By outsourcing complex security management, your internal teams are free to concentrate on their primary functions: driving revenue, developing products, and serving customers.
Engaging a consultancy is not an admission of internal deficiency. It is a strategic decision to leverage external, specialised expertise to achieve business objectives more rapidly and build resilience more efficiently.
This model allows your organisation to benefit from best-in-class security without bearing the full burden of its creation. It has also spurred innovative service models, such as managed security services and outcome-based pricing, where the consultancy's success is directly aligned with your business results.
Ultimately, this strategy converts a market-wide problem into a powerful catalyst for your company's growth.
A Practical Framework for Vendor Selection
Selecting a cyber security consultancy is a strategic decision with a direct impact on your capacity for innovation and competitive positioning. A superficial review of service catalogues and hourly rates is insufficient. A robust, business-centric framework is required to identify a partner that not only addresses technical vulnerabilities but also aligns with your strategic objectives and operational methodologies.
This process should be viewed as a strategic assessment rather than a procurement task. The objective is to evaluate a potential partner's depth of expertise, commercial model viability, and collaborative capacity. The goal is to find a consultancy that operates as a co-preneur, sharing accountability for business outcomes rather than simply delivering a report.
The following checklist provides senior decision-makers with a structured approach to asking the right questions, covering technical competence, industry knowledge, and the commercial terms of engagement.
Evaluating Technical and Strategic Depth
The initial step is to confirm the consultancy possesses the forward-looking expertise required for a modern enterprise, particularly one leveraging AI. Generic security advice is obsolete.
Begin by examining their approach to AI security and compliance. How do they secure the entire AI lifecycle, from data ingestion and model training to deployment and ongoing monitoring? Their response should articulate a clear, practical methodology for managing risks such as model poisoning or data leakage, while maintaining compliance with regulations like the EU AI Act.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
Next, inquire about their specific experience with compliance mandates relevant to your industry. For German automotive or manufacturing firms, for instance, a profound understanding of TISAX (Trusted Information Security Assessment Exchange) is non-negotiable. Request detailed case studies where they guided a company through the TISAX certification process, focusing on how they translated complex requirements into practical, operational controls.
Finally, assess their approach to knowledge transfer. A true partner enhances your internal team's capabilities, rather than fostering dependency. What mechanisms do they employ—joint workshops, paired programming, embedding personnel? A demonstrable commitment to enablement is a key indicator of a genuine partnership orientation.
This decision tree illustrates the initial choice: build an in-house team or engage a consultancy to bridge the talent gap.
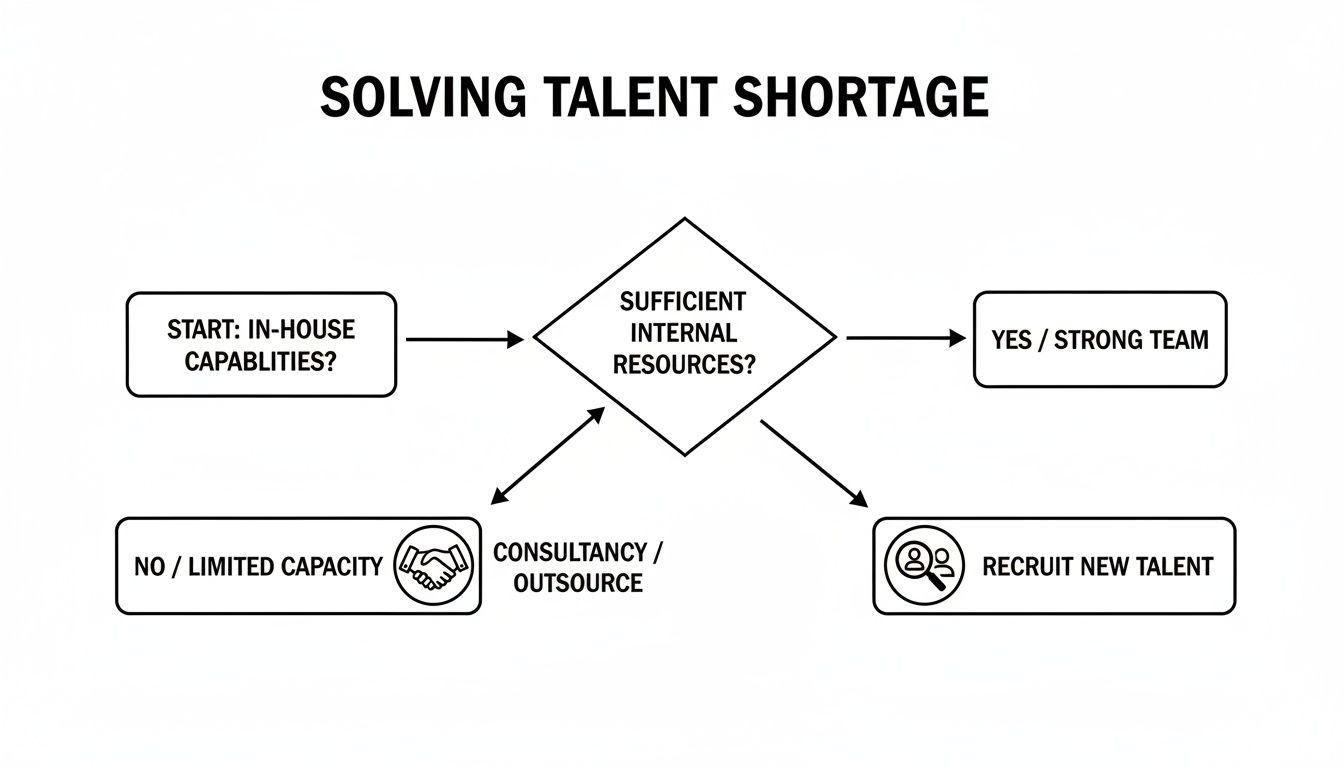
The flowchart clarifies that the "make-or-buy" decision is the foundational step in addressing the cybersecurity skills gap. For a more in-depth exploration of this decision, our guide on conducting a detailed make-or-buy analysis may be beneficial.
Defining Commercial and Performance Metrics
Once technical competence is established, the discussion must shift to commercial terms. This is where you define how success will be measured and how value will be delivered. The objective is to move beyond simplistic metrics to Key Performance Indicators (KPIs) that reflect tangible business impact.
The most effective security KPIs are directly linked to business objectives. Instead of merely counting patched vulnerabilities, measure the reduction in time-to-market for a new product, or the successful audit that enabled entry into a new market.
Discussing KPIs forces a conversation about the definition of "value." A consultancy focused on business outcomes will embrace this dialogue. One accustomed to selling blocks of time may be less forthcoming.
It is also critical to understand their pricing models and flexibility. While project-based or time-and-materials contracts are standard, explore whether they offer outcome-based or retainer models that create aligned incentives. Does their pricing structure ensure mutual success?
Lastly, establish realistic project timelines and milestones. A credible consultancy will present a clear roadmap with distinct phases, deliverables, and review points. This structured governance ensures transparency and allows for adjustments, transforming the engagement from an opaque process into a predictable, collaborative partnership.
Building a Resilient, Innovative Future
The discourse surrounding cyber security has fundamentally changed. It is no longer a technical niche confined to the IT department, focused on firewalls and incident response. For German leadership, security is now an integral component of business strategy, directly influencing an organisation's capacity for growth, competition, and long-term innovation.
Selecting from the various cyber security consultancies is now a C-suite-level strategic decision. The challenge is not merely to procure a service, but to identify a partner whose strategic orientation aligns with your commercial objectives. This choice will determine the velocity and safety with which you can adopt new technologies—particularly AI—without exposing the enterprise to catastrophic risk.
From Defensive Wall to Innovation Engine
Forward-thinking leaders no longer view security as a reluctant necessity. They see it as the foundation for growth. A robust, intelligent security framework provides the confidence to pursue new markets, de-risk the innovation lifecycle, and build unwavering trust with customers and partners. It transforms security from a protective shield into a powerful business accelerator.
This is where the 'co-preneur' partnership model proves its value. A standard vendor executes a list of tasks. A co-preneur, in contrast, shares accountability for your business success. They integrate security into your corporate DNA from inception, ensuring that new products and AI initiatives are secure by design, not remediated as a reactive measure.
The true measure of a security partnership is not its ability to prevent every attack, but its capacity to enable progress. The right partner helps you move faster, not slower, by making security an intrinsic part of your growth engine.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
Your Next Strategic Move
As you plan for the future, the critical question is not simply, "How do we protect our current assets?" but rather, "Who will partner with us to build a more resilient and innovative future?" The answer lies with partners who possess an entrepreneurial mindset themselves.
Seek a consultancy that will challenge existing paradigms, bring a builder's mentality to the table, and be willing to align their success directly with yours. This is how your security posture transcends mere defence to become a strategic asset, fuelling your prosperity and providing a distinct competitive advantage in the age of AI.
Frequently Asked Questions
When evaluating cyber security consultancies, executive-level questions extend beyond technology to focus on business outcomes. How does this partnership mitigate risk? How does it accelerate our innovation agenda? This section addresses the strategic inquiries that leaders have when considering a security partner.
How Does a Consultancy Help Us Implement AI Securely?
An effective consultancy does not append security to your AI projects as an afterthought. This approach creates delays and operational friction. Instead, they integrate security into your AI roadmap from the outset—a concept known as 'Security by Design'.
This methodology functions not as a barrier, but as a guardrail for innovation, providing your teams with the confidence to pursue advanced AI initiatives while managing risks proactively. This typically involves:
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
- Securing Data Pipelines: Ensuring the integrity and confidentiality of data used to train AI models to prevent data poisoning or leakage.
- Hardening AI Models: Implementing defences against sophisticated attacks designed to manipulate or compromise your AI systems.
- Ensuring Compliance: Maintaining your AI applications' adherence to major regulations like GDPR and the forthcoming EU AI Act, which is a critical business requirement.
What Is the Difference Between an Audit and a Partnership?
This is a critical distinction that determines the nature of the value received. The difference lies in the scope, duration, and ownership of outcomes.
An audit is a point-in-time assessment. A consultant evaluates your systems against a predefined checklist and delivers a report of their findings. It is a tactical, useful exercise for a specific purpose, but the engagement concludes upon delivery of the report.
A security partnership, conversely, is a continuous, collaborative relationship. The consultant becomes an extension of your team, providing ongoing strategic advice, helping to develop internal capabilities, and, crucially, sharing accountability for achieving your business objectives.
The focus shifts from merely identifying problems to building an organisation with the enduring capacity to manage future challenges.
How Do We Measure the ROI of a Security Consultancy?
Measuring the return on investment for security initiatives requires looking beyond conventional technical metrics. It necessitates a direct correlation between security activities and business performance.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
True value is demonstrated through business-centric KPIs. Instead of tracking patched vulnerabilities—a metric with limited relevance to the boardroom—the focus should be on outcomes that matter.
Effective ROI indicators include:
- Accelerated Time-to-Market: By how much did we reduce the launch time for a new digital product because security was integrated from the start?
- Cost Avoidance: What is the quantified financial impact of a breach in our sector, and what is the value of preventing such an incident?
- Business Enablement: Did achieving a key certification like TISAX unlock a new market or secure a major client that was previously unattainable?
- Operational Efficiency: What are the quantifiable time and cost savings realised from streamlined and automated security processes?
Ultimately, the most significant return is the ability to innovate securely while safeguarding the brand and reputation that are foundational to long-term growth.
At Reruption GmbH, we act as co-preneurs, embedding AI security and compliance into your innovation lifecycle to drive growth and build resilience. We take shared accountability for business outcomes, turning your security posture into a competitive advantage. Learn how our co-preneur model can accelerate your AI initiatives.