A cyber security consultation is the strategic engagement of specialists to conduct a comprehensive assessment of an organisation's digital resilience. This process transcends superficial diagnostics, stress-testing the entire digital infrastructure to identify latent vulnerabilities. The outcome is a clear, actionable roadmap designed to fortify defences and align security posture with strategic business objectives.
The engagement functions as a strategic partnership. The primary objective is not merely to remediate vulnerabilities but to integrate security measures directly with corporate ambitions, particularly in the context of adopting transformative technologies like Artificial Intelligence. Executed correctly, this transforms security from a necessary operational expenditure into a distinct competitive advantage.
Why Cyber Security Consultation Is a Strategic Imperative

In an economic landscape where data and AI are primary assets, cyber threats have evolved from IT-level disruptions to existential business risks. Legacy, static security protocols are fundamentally inadequate to counter the velocity and sophistication of modern, AI-driven attacks. For German enterprises, addressing this reality is a matter of strategic survival.
The market data substantiates this urgency. The German cyber security market, valued at approximately USD 13.60 billion, is projected to expand to USD 37.90 billion by 2033. This growth reflects a stark operational reality: 65% of companies in Germany now classify cyberattacks as an existential threat. The financial impact of these attacks recently reached an unprecedented EUR 178.6 billion in a single year, rendering expert guidance an indispensable component of modern governance.
Shifting from Defence to Strategic Advantage
A modern cyber security consultation extends far beyond traditional checklist audits or vulnerability scans. It constitutes a strategic partnership focused on transitioning an organisation's security posture from a reactive, defensive stance to a proactive enabler of growth. This paradigm reframes security as a foundational pillar for achieving key corporate objectives.
This strategic orientation is critical for any organisation committed to innovation and long-term value creation. An effective consultation enables a business to:
- Safely Adopt AI: Deploy novel AI systems and tools with full confidence, ensuring data integrity and mitigating inherent risks from the initial design phase.
- Protect Intellectual Property: Safeguard critical assets—including proprietary algorithms, R&D data, and strategic plans—from sophisticated corporate espionage.
- Enable Market Expansion: Meet the stringent security and compliance mandates required for entry into new markets or critical supply chains, such as the automotive industry's TISAX requirements.
A proactive, deeply integrated security strategy is no longer optional. It is the bedrock upon which resilient, forward-thinking organisations are built, enabling them to de-risk innovation and secure their competitive edge.
The Role of a Co-Preneurial Partner
The traditional consulting model—delivering a report and disengaging—is obsolete in today's dynamic threat landscape. What is required is a genuine partner, a "Co-Preneur" who assumes shared accountability for business outcomes, not merely the completion of security tasks.
This approach fosters deep integration with internal teams, enhancing their capabilities and ensuring every security initiative is directly linked to value creation. By understanding this distinction, leadership can better select a cyber security consultant who is fundamentally invested in the organisation's long-term success.
Understanding the Scope of a Modern Consultation

A contemporary cyber security consultation has evolved significantly beyond the legacy practice of executing a vulnerability scan and delivering a static report. For today’s C-suite, it is a strategic partnership engineered to build enterprise resilience, particularly as transformative technologies like AI become integral to operations. The objective is to navigate complex threat vectors and directly align security investments with business growth.
This engagement is best understood not as a one-time audit, but as a collaborative architectural review of the entire digital enterprise. A high-value consultation analyses an organisation's unique risk profile to construct a security posture that is robust today and adaptable for tomorrow. It is a comprehensive assessment of technology, personnel, and processes as an interconnected system.
This holistic methodology is structured around several key pillars, each designed to address specific risk domains and uncover strategic opportunities.
Core Pillars of a Strategic Consultation
A truly valuable engagement is predicated on rigorous analysis and forward-looking strategic planning. These core services are not a checklist but a synergistic framework for weaving a cohesive security fabric that protects current assets while preparing for future challenges. Each component provides a distinct but critical layer of insight.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
The foundational pillars typically include:
- Strategic Risk Assessment: The engagement commences here. We collaborate with leadership to identify "crown jewel" assets—the most valuable data, systems, and workflows—and then quantify the business impact of their potential compromise.
- Penetration Testing (Ethical Hacking): This serves as the ultimate validation of existing controls. We execute controlled, real-world attack simulations to identify and remediate exploitable vulnerabilities in networks and applications before malicious actors can.
- Security Architecture Review: This is analogous to reviewing the blueprints of a fortress before construction. We analyse existing or proposed system designs to ensure security is an intrinsic element from inception, not an afterthought.
- Incident Response Planning: Given the inevitability of security events, preparation is paramount. This service establishes a clear, actionable playbook detailing roles and responsibilities during a breach to minimise impact and accelerate recovery.
Together, these pillars provide a 360-degree perspective on an organisation's security health, from high-level strategic risks to granular technical configurations.
Adapting to AI and Complex Compliance
The integration of AI introduces novel security challenges that traditional frameworks were not designed to address. A modern cyber security consultation must directly confront these specific risks, ensuring that innovation does not inadvertently create new threat vectors. This involves examining everything from the security of large language models (LLMs) to the integrity of training data. A deeper understanding of these specialised services for AI security and compliance clarifies how to effectively de-risk AI adoption.
In the AI era, security is not just about protecting data; it's about ensuring the trustworthiness and reliability of the intelligent systems that will drive future business decisions. This requires a new playbook for governance and risk management.
Furthermore, compliance is a significant driver for enterprises in Germany and across Europe. Frameworks such as TISAX for the automotive supply chain or the globally recognised ISO 27001 are not merely best practices; they are often prerequisites for market participation.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
A critical component of this is navigating data protection regulations like GDPR, particularly as AI is introduced. For a more detailed analysis, this practical AI GDPR compliance guide provides valuable insights. A proper consultation ensures security measures are not only effective but fully compliant, transforming a regulatory burden into a demonstrable competitive advantage and a signal of corporate trustworthiness.
From High-Level Strategy to Hands-On Execution
A cyber security consultation is not a project; it is a partnership. A well-defined proposal serves as the blueprint for this partnership, translating broad business objectives into a concrete execution plan with measurable outcomes. For executive leadership, understanding this process is essential for evaluating commitment, tracking milestones, and ensuring the result is a more resilient organisation, not merely a report.
The engagement is designed to progress logically through distinct phases. This structured methodology eliminates ambiguity and creates a clear project charter. It guarantees that every action, from technical analysis to policy development, directly supports the strategic goals established at the outset. The overarching aim is to build internal capability, not to create long-term consultant dependency.
Phase 1: Scoping and Strategy
The engagement commences not with technology, but with strategic dialogue. The initial step is a collaborative workshop that convenes key stakeholders from leadership, IT, and operations. The objective is to establish a shared understanding of the business context, risk appetite, and strategic priorities, especially regarding AI adoption and data governance.
During this phase, we work jointly to identify the organisation's "crown jewels"—the critical assets, data, and processes essential for business continuity. Subsequently, we formalise the engagement's scope, defining the specific systems, departments, and compliance frameworks (e.g., TISAX, ISO 27001) to be addressed. This culminates in a formal Statement of Work (SoW), our shared charter outlining objectives, timelines, and rules of engagement.
Phase 2: Technical Assessment and Analysis
With a clear strategy in place, the focus shifts to a deep technical evaluation. This phase involves a rigorous, evidence-based assessment of the current security posture. It is a multi-faceted approach, combining automated scanning with the indispensable insights of manual expert analysis. We conduct penetration tests, review architecture, and audit configurations to uncover latent vulnerabilities that threat actors could exploit.
This stage functions as a comprehensive diagnostic of the company's security health, producing an objective snapshot of the current state. The findings are then prioritised based on the business context established in Phase 1, distinguishing theoretical risks from genuine, high-impact threats. The key deliverable is a Technical Findings Report that not only lists vulnerabilities but also articulates their potential business impact in clear, executive-level language.
Phase 3: Building a Strategic Roadmap
This is the phase where analysis translates into actionable strategy. Leveraging insights from the technical assessment, we collaborate with your team to construct a security roadmap that is both ambitious and achievable. This is not a generic template; it is a customised plan tailored to your budget, operational realities, and strategic timeline.
The roadmap outlines a clear sequence of initiatives, including immediate "quick wins" to reduce risk exposure and longer-term projects to build foundational security capabilities for the future.
The goal is to create a multi-year strategy that balances immediate fixes with the sustainable development of a mature security programme. This ensures security improvements are iterative and manageable, delivering continuous progress without disrupting business operations.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
The primary deliverable is the Strategic Security Roadmap—a detailed plan complete with prioritised actions, resource estimates, and the metrics for measuring success. For additional context on structuring such complex initiatives, our guide on the principles of system engineering for IT projects offers a relevant framework.
A well-structured consultation progresses from broad strategy to specific technical details and back to a strategic implementation plan. The table below summarises this phased flow, ensuring each step has a clear purpose and tangible outcome.
Cyber Security Consultation Engagement Phases
| Phase | Primary Objective | Key Activities | Key Deliverable |
|---|---|---|---|
| 1. Scoping & Strategy | Define business context and align on goals. | Stakeholder workshops, asset identification, risk appetite definition, scope confirmation. | Statement of Work (SoW) |
| 2. Technical Assessment | Uncover and analyse security vulnerabilities. | Penetration testing, architecture review, configuration audits, threat modelling. | Technical Findings Report |
| 3. Roadmap Development | Create a prioritised, actionable improvement plan. | Risk prioritisation, solution design, budget and resource planning. | Strategic Security Roadmap |
| 4. Implementation | Execute the roadmap and empower the team. | Policy drafting, tool configuration, knowledge transfer, team training. | Strengthened Security Posture |
Each phase builds directly upon the preceding one, transforming ambiguity into a clear, predictable, and value-driven engagement. This is the foundation of a true Co-Preneurial partnership.
Phase 4: Implementation and Enablement
Finally, the strategic roadmap is translated into operational reality. A true Co-Preneurial partner does not conclude the engagement with a list of recommendations. We become actively involved in implementing the controls and processes designed in collaboration. This is a hands-on phase where we guide internal teams, assist in configuring new security technologies, draft policies, and, most critically, transfer knowledge.
Germany's cyber security market is projected to reach USD 23.89 billion by 2030. Large enterprises are driving this trend, with 73% planning to increase security spending, particularly to secure new AI and LLM applications on self-hosted infrastructure. A significant part of this enablement phase is ensuring your organisation possesses the requisite skills to manage these advanced systems securely. The end goal is not merely a completed task list, but a demonstrably strengthened security posture, an empowered internal team, and a clear methodology for ongoing security management and improvement.
How to Select the Right Security Partner
Selecting a cyber security consultation partner is a critical decision for any leadership team. The right partner becomes a strategic asset—an extension of the organisation that de-risks innovation and accelerates growth. The wrong choice results in costly reports, a false sense of security, and a widening gap between deployed defences and actual threats.
An effective evaluation must look beyond certifications and vendor accolades. The assessment should focus on three core areas: the firm's partnership philosophy, its technical mastery in modern domains like AI, and its commitment to accountability for business outcomes. This framework distinguishes a true partner from a mere vendor.
Beyond the Proposal: A Partnership Philosophy
A proposal is merely the starting point. The true measure of a potential partner is their operating model. Do they function as an external advisor who delivers a report and disengages? Or do they embed themselves as a "Co-Preneur," sharing accountability for the outcomes?
This distinction is paramount. A true partner invests time upfront to understand your business objectives, ensuring every technical recommendation directly supports strategic goals. This philosophy is evident in their engagement structure. Look for a model built on collaboration and knowledge transfer. Their primary objective should be to strengthen your internal teams, not to create a permanent dependency.
A partner’s value isn’t measured by the thickness of their final report, but by the enhanced capabilities and resilience of your own team long after the engagement ends. They should build you up, not lock you in.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
The consultation process itself reveals much about their approach. This flow chart illustrates a typical, outcome-focused engagement that progresses from strategic alignment through to hands-on enablement.
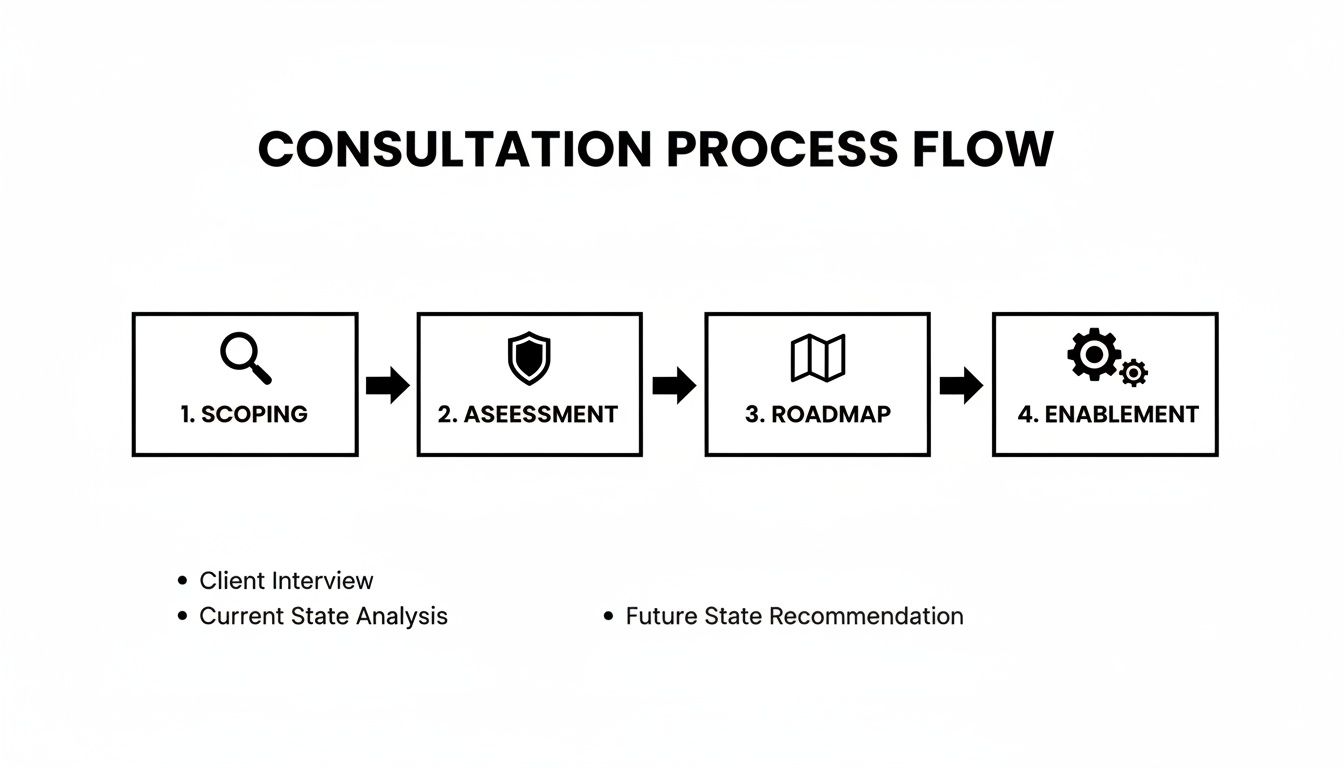
Each phase, from Scoping to Enablement, should be executed as a collaborative effort designed to build momentum and deliver tangible value at every stage.
Assessing Technical Acumen and Track Record
Strategic alignment is meaningless without the technical expertise to execute. Your partner must possess deep, demonstrable experience not only in foundational security disciplines but also in the specific technologies that drive your business—particularly AI. A key indicator is their approach to building secure systems from inception. When vetting potential partners, inquire about their experience with robust secure code review practices as a core component of development.
Key questions for vetting potential partners include:
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
- Production Systems: Can you provide case studies of production-grade AI or data-intensive systems you have secured, beyond simple audits?
- Compliance Mastery: How have you guided clients through complex compliance journeys like TISAX or ISO 27001, linking technical controls to business requirements?
- Team Enablement: What is your methodology for training and upskilling our teams on new security tools and processes?
- Incident Experience: Describe a complex security incident you helped a client navigate. What was your role, and what was the business outcome?
Their responses should demonstrate a history of practical, hands-on application, not just theoretical knowledge. You are seeking proof of their ability to navigate real-world challenges and deliver measurable improvements. For a deeper analysis, review our detailed examination of what distinguishes the top-tier cyber security consultants.
A Checklist for Executive Evaluation
To structure your final decision, use this checklist to compare potential partners. It is designed to move beyond standard qualifications and focus on indicators of strategic fit and a commitment to shared success.
- Strategic Alignment: Do they clearly articulate how their security recommendations will support our specific business goals, such as AI innovation or market entry?
- Co-Preneurial Model: Is their engagement model based on shared accountability and internal team enablement, or is it a transactional, report-for-fee service?
- Proven AI & Modern Tech Expertise: Have they demonstrated hands-on experience securing complex, production-grade systems analogous to ours?
- Clear Communication: Can they explain complex technical risks and strategic roadmaps in a manner that resonates with both engineering teams and the board of directors?
- Cultural Fit: Does their team exhibit the entrepreneurial agility and collaborative spirit required to integrate effectively with our corporate culture?
Choosing the right cyber security consultation firm is an investment in your company’s future. By applying this strategic evaluation framework, you can identify a partner who will not only protect your assets but actively contribute to building a more secure, resilient, and competitive enterprise.
Measuring the ROI of Your Security Investment
How does one measure the value of a crisis that was averted? For executives, this question is central to justifying an investment in a cyber security consultation. The return is not always captured on a profit and loss statement; it is measured in resilience, reputation, and the strategic freedom to innovate without fear.
A true partnership shifts the conversation from cost to value. It reframes security not as an operational expense, but as a direct enabler of business objectives. To make this tangible for the C-suite, it is essential to define success metrics—both quantitative and strategic—that clearly demonstrate how a proactive security posture fuels sustainable growth.
Tangible Success Metrics
The most direct measures of ROI are quantifiable improvements in security performance and operational efficiency. These are the hard numbers that validate risk mitigation and cost avoidance, forming the foundation of the business case.
A Co-Preneurial security partner focuses on delivering measurable results:
- Reduction in Security Incidents: The primary objective is a dramatic reduction in the frequency and severity of security incidents, from phishing attempts to major breaches. Tracking this metric provides a clear indicator of defensive efficacy.
- Accelerated Recovery Times: When an incident occurs, response velocity is critical. A well-architected incident response plan, developed with an expert partner, can reduce system downtime from days to hours, mitigating significant operational and financial losses.
- Successful Compliance Audits: Achieving certifications like ISO 27001 or TISAX is not a perfunctory exercise. It is a tangible outcome that unlocks new markets, particularly within the demanding German automotive supply chain. A successful audit is a clear pass/fail metric of the consultation's value.
Currently, large enterprises represent 71.9% of Germany's cybersecurity expenditure, but the SME sector—the backbone of the economy—is projected to increase its share to 36% by 2030. A significant obstacle remains: only 39% of SMEs are ISO 27001 certified, though 61% are actively pursuing it. This is where an expert cyber security consultation provides a direct path to closing that gap and securing a competitive position. Further insights on the German cybersecurity market and its growth drivers here are available.
Intangible Value and Strategic Freedom
Beyond quantitative metrics, the most profound ROI often derives from the strategic advantages and enhanced reputation afforded by a strong security posture. While more difficult to quantify, these benefits are what truly empower an enterprise to lead its industry.
A robust security framework isn’t a set of handcuffs; it’s the solid foundation that gives your business the freedom to chase ambitious goals, embrace new technologies like AI, and build unbreakable trust with customers and partners.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
This strategic value manifests in several key areas:
- A Fortified Brand Reputation: In an era where a single breach can erode decades of goodwill, a reputation for impeccable security becomes a significant competitive differentiator.
- Enhanced Customer Trust: Demonstrating a serious commitment to protecting customer data fosters loyalty and positions the company as a preferred partner.
- The Confidence to Innovate Boldly: A secure-by-design culture enables teams to experiment with AI and other emerging technologies without being constrained by risk, accelerating time-to-market.
By directly linking security initiatives to these business outcomes, a true partner ensures the investment yields dividends long after the initial engagement, securing the future of the organisation.
Building Your Strategic Path to a Secure Future
For German business leaders, the imperative is clear: proactive cyber security is no longer a defensive measure but a significant competitive advantage. Navigating this landscape requires moving beyond traditional vendor relationships. The age of AI demands a new partnership model—one where a cyber security consultation firm operates as a strategic co-pilot, sharing accountability for business outcomes.
This paradigm shift transforms security from an expense item into a core pillar of the growth strategy. When security is integrated into the corporate DNA, the organisation gains the freedom to innovate with confidence. It can adopt new AI tools without hesitation and build unwavering trust with customers and partners. The right partner does not simply deliver a report; they enhance the capabilities of your team, de-risk strategic projects, and ensure every security investment drives measurable value.
From Risk Management to Value Creation
A true Co-Preneurial partner helps reframe the entire security conversation. The question evolves from, "How much will this cost?" to, "What new opportunities will this enable?"
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
This shift in perspective is transformative. It empowers an organisation to:
- Accelerate Innovation: Deploy AI and other advanced systems with confidence, knowing they are secure by design from day one.
- Strengthen Market Position: Achieve stringent compliance standards like TISAX, opening access to critical supply chains and new markets.
- Enhance Brand Reputation: Leverage a commitment to security as a powerful market differentiator that attracts and retains customers.
Ultimately, the goal is to build an organisation that is not merely protected, but prepared to lead. A strong security posture is the engine that drives sustainable growth and resilience.
Investing in a strategic cyber security consultation is an investment in your organisation’s future. It is the decisive step towards securing your leadership position in a world where digital trust is the ultimate currency.
The journey begins with the recognition that security and innovation are two sides of the same coin. For a deeper examination of building frameworks capable of withstanding scrutiny, consult our guide to enterprise AI security for 2025. By selecting a partner who shares your entrepreneurial drive, you are not just procuring a service—you are architecting a strategic path to a secure and prosperous future.
Your Questions, Answered
When considering a cyber security consultation, several key questions invariably arise. For managers and C-level leaders in Germany, these are critical inputs for making a sound strategic decision. Here is a direct assessment of what to expect when investing in a high-calibre security partner.
What is the typical cost of a Cyber Security Consultation in Germany?
To be direct, the investment is directly correlated with the scope of work. A foundational risk assessment for a medium-sized enterprise may begin in the low five-figure range. However, a comprehensive engagement involving advanced penetration testing, an AI system architecture review, and preparation for a formal TISAX audit represents an investment ranging from €50,000 to over €250,000.
The absolute number is secondary to the value returned. A credible partner will provide a scope of work that draws a clear line from every euro invested to a specific, measurable security improvement. The focus is on linking the investment directly to tangible business protection.
What is the expected duration of an engagement?
The timeline, like the cost, is contingent upon the scope. A focused penetration test can often be concluded within two to four weeks. A more comprehensive security architecture review may require four to eight weeks. A full strategic program to achieve ISO 27001 or TISAX readiness represents a more significant commitment, typically spanning a six to twelve-month engagement.
However, a premier partner will not delay the delivery of value. Initial findings and high-impact, actionable insights should be delivered within the first few weeks, enabling immediate risk reduction and iterative progress.
This methodology builds momentum and ensures a return on investment is realised almost immediately.
We have a capable internal IT team. Why engage an external consultant?
This is a valid consideration. The purpose of an external partner is not to replace your team, but to augment its capabilities in three critical areas.
First, consultants possess deep, specialised knowledge of the global threat landscape and complex compliance frameworks like TISAX. It is their sole focus to remain ahead of emerging threats and regulatory changes, bringing a level of expertise that is difficult and cost-prohibitive to maintain in-house. Second, they provide an objective, third-party perspective. Unencumbered by internal politics or historical context, they can offer an unvarnished assessment of an organisation's true risk posture.
Finally, a strategic partner functions as an accelerant. They expedite critical projects and transfer specialised skills in areas like AI security, thereby strengthening your internal team's resilience and equipping them for future challenges.
At Reruption, we are not just consultants; we are Co-Preneurs. We share accountability for your business outcomes. We do not deliver a report and disengage—we integrate with your team to build a more resilient, secure, and innovative organisation. See how our approach can secure your path to growth at https://www.reruption.com.