For C-level executives in Germany's leading enterprises, cybersecurity has transcended its traditional role as an IT budget line item. It is now a cornerstone of business strategy, resilience, and competitive differentiation. Engaging expert cyber security consultants is no longer a reactive measure; it is a strategic imperative to safeguard core operations, intellectual property, and market reputation.
The Evolution of Cyber Security Consultants into Strategic Partners
In an economy increasingly driven by digitalisation and artificial intelligence, the paradigm has shifted. Cyber security consultants are no longer merely technical specialists engaged to remediate vulnerabilities. They have become indispensable strategic partners who integrate security principles directly into core business objectives. This evolution is about transforming security from a cost centre into a tangible competitive advantage.
This strategic realignment is critical, particularly for German enterprises navigating complex regulatory landscapes and persistent cyber threats. The economic impact is undeniable: recent data estimates the annual damages from cybercrime at a staggering €178.6 billion. This pressure is catalysing significant growth in the security sector, with the market projected to expand at a CAGR of 8.20% through 2034, signalling a clear direction for corporate investment priorities. Further insights into the German cybersecurity market and its projected growth here are available.
Aligning Security with Core Business Objectives
A truly strategic consultant focuses on enabling business initiatives, not obstructing them. Their value is measured by their ability to provide clear, actionable answers to critical executive-level questions:
- How can we deploy AI to enhance manufacturing intelligence without introducing unacceptable operational or data risks?
- What is the quantifiable business impact—in terms of financial loss and operational disruption—of a potential data breach?
- How does a robust security posture strengthen our compliance position with regulators and auditors for standards like TISAX or ISO?
By translating technical complexities into the language of business impact—articulating risks in terms of revenue loss, operational downtime, and brand equity—these experts provide leadership with the clarity required for decisive strategic action. They ensure every euro invested in security is directly correlated with value protection and creation.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
Ultimately, the right cyber security consultants enable the pursuit of new opportunities. They provide the confidence and framework necessary to undertake ambitious digital transformation projects, from AI-driven automation to supply chain digitalisation, ensuring the security architecture functions not just as a shield, but as an engine for sustainable growth and innovation.
Mapping Consulting Services to Business Risk
From a leadership perspective, the value of a cyber security consultant is not defined by technical jargon, but by the direct correlation of their services to tangible business outcomes.
The critical question for any executive is not what a service does, but what business risk does it mitigate and what strategic opportunity does it unlock? This perspective shifts the discourse from a technical cost analysis to a strategic necessity, ensuring every security investment is aligned with corporate resilience and growth objectives.
Consider a penetration test. At a technical level, it is a vulnerability assessment. Strategically, it is a controlled stress test of your digital operations, simulating a real-world attack to identify weaknesses before adversaries can exploit them. The business outcome is not a voluminous technical report, but a prioritised, actionable roadmap to fortify revenue-generating systems and protect critical intellectual property.
Similarly, a managed Security Operations Centre (SOC) can be viewed as a monitoring service. A more accurate strategic description is a ‘digital command centre’. A high-performing SOC provides continuous vigilance and, crucially, a rapid response capability to neutralise threats at inception. For leadership, this translates directly into a material reduction in the risk of a catastrophic data breach or prolonged operational disruption.
Clarifying Value Beyond Technical Audits
This strategic mindset extends to proactive governance and compliance activities. Pursuing certification for standards like TISAX or ISO 27001 can often be perceived as a regulatory burden—a compliance checkbox.
However, a strategic consultant reframes this as a powerful market differentiator. In the German automotive and manufacturing sectors, such certification is a critical signal of operational excellence and trustworthiness. It builds immediate confidence with key partners and clients by demonstrating that your commitment to security is substantive and verifiable.
For any leadership team committed to integrating AI, these services are non-negotiable. They establish the essential guardrails for innovation, ensuring new AI-driven processes are secure and compliant by design. This proactive approach preempts costly and disruptive reactive fixes, minimising the risk of a data misuse incident that could inflict long-term brand damage.
The diagram below illustrates this strategic evolution of security's role within an organisation.
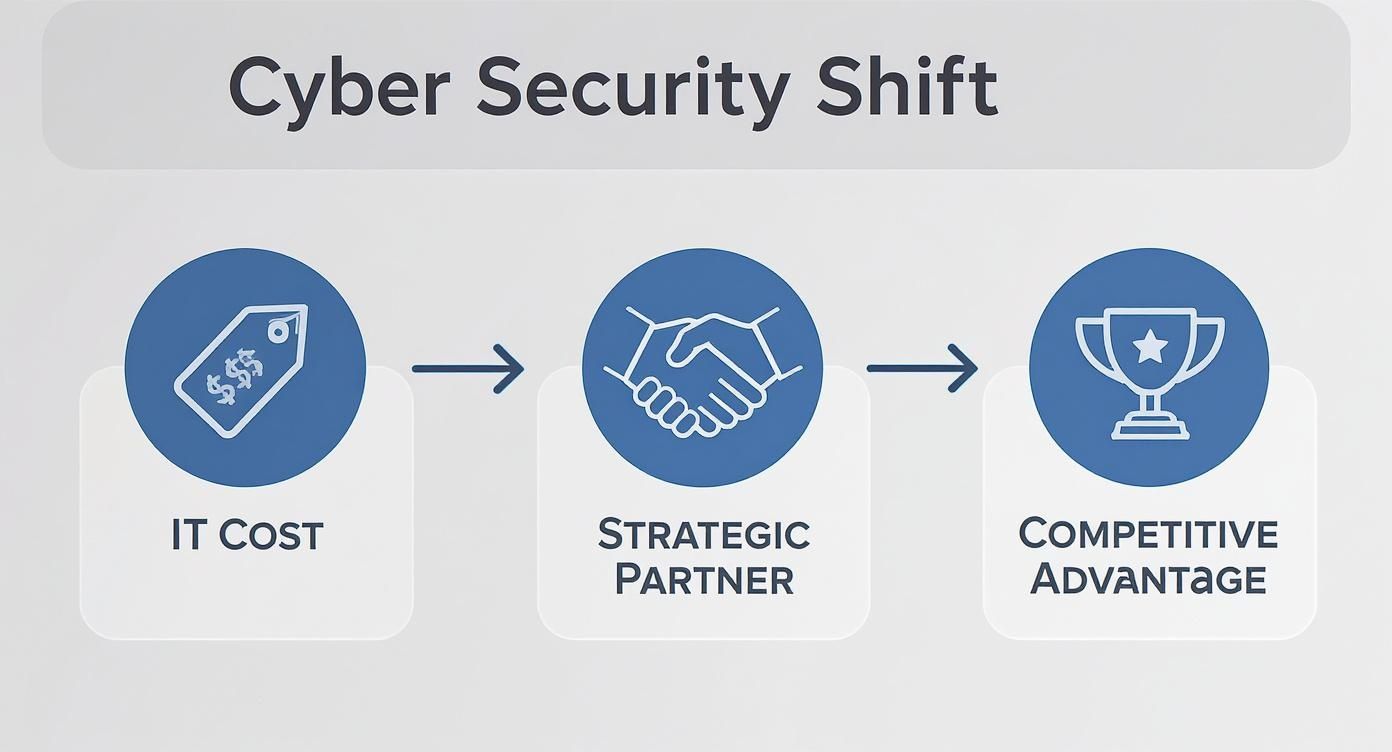
This is a necessary evolution. Security ceases to be an isolated IT cost and becomes a strategic enabler of competitive advantage. Every service, when mapped to a specific business risk, contributes to this transformation. By asking the right questions—and demanding answers that link technical actions to business impact—you can ensure your engagement with cyber security consultants delivers measurable, strategic value.
Core Cyber Security Consulting Services and Business Outcomes
To crystallise this connection, the following table maps common consulting services directly to the business problems they solve for enterprise leadership.
| Consulting Service | Business Problem Addressed | Key Outcome for Management |
|---|---|---|
| Penetration Testing & Red Teaming | "Are our critical digital assets secure against a sophisticated and determined attacker?" | A prioritised, actionable roadmap to remediate vulnerabilities before they can be exploited, safeguarding revenue and IP. |
| Managed SOC (Security Operations Centre) | "How can we achieve 24/7 threat detection and response without building a cost-prohibitive internal team?" | Significantly reduced risk of a costly data breach and operational downtime through continuous monitoring and expert incident response. |
| ISO 27001 / TISAX Compliance | "How do we formally demonstrate our security commitment to key partners, particularly within the automotive supply chain?" | Achieved certification that serves as a market differentiator, builds partner trust, and unlocks access to new business opportunities. |
| Virtual CISO (vCISO) | "We require executive-level security strategy and leadership but are not prepared for a full-time C-level appointment." | Access to executive-grade strategic guidance that aligns security initiatives with core business goals on a flexible, outcome-focused basis. |
| AI Security & Governance | "How do we leverage AI for innovation without exposing the enterprise to new data privacy, security, and compliance risks?" | A secure and compliant framework for AI adoption, preventing costly remediation and reputational damage from data misuse or model failure. |
This table serves as a framework for translating technical activities into the language of business risk, operational resilience, and competitive advantage.
How to Select the Right Consulting Partner
Selecting the right cyber security consultants is not a procurement exercise; it is a strategic decision with long-term implications. The ideal partner functions as an extension of your leadership team, contributing specialised expertise that aligns seamlessly with your business objectives.
For German enterprises, particularly within the automotive and manufacturing sectors, the stakes are exceptionally high, demanding a commensurately rigorous evaluation process.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
The selection process must transcend a superficial comparison of service catalogues. It requires a deep assessment of a potential partner’s demonstrable, industry-specific expertise. Do they possess a nuanced understanding of production environments and the unique challenges of securing operational technology (OT)? Can they provide evidence of certifications and a proven track record in navigating the German and EU regulatory landscape, from GDPR to the NIS2 Directive?

Beyond Technical Proficiency
A critical, often overlooked, factor is communication efficacy. The consultant must be capable of translating complex technical findings into clear, actionable insights for a non-technical board-level audience.
A partner who communicates exclusively in technical jargon offers limited strategic value. The partner you require is one who can articulate risk in terms of financial impact, operational continuity, and brand reputation—the language of the C-suite.
The current German market presents an additional challenge. The nation faces a significant shortage of cyber security specialists, with an estimated 109,000 vacancies for IT experts. One recent study revealed that 85% of firms report difficulty in recruiting qualified personnel, and only 10% believe they have sufficient access to IT security talent.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
This talent scarcity directly affects the quality and availability of consulting firms, making a meticulous evaluation process all the more critical. You can find more details on the German IT talent shortage from ibisworld.com.
An elite consulting partner not only provides their own top-tier talent but also acts as a force multiplier for your internal teams, transferring knowledge and elevating the entire organisation's security posture and capabilities.
Identifying Red Flags in the Evaluation Process
During discussions with potential cyber security consultants, be vigilant for indicators of a transactional mindset rather than a strategic partnership. These red flags can help filter out firms ill-equipped to meet the demands of a modern enterprise.
- Generic, Boilerplate Proposals: A one-size-fits-all approach demonstrates a fundamental lack of interest in understanding your specific business context, challenges, and risk profile.
- Failure to Articulate ROI: If a firm cannot clearly articulate how its services deliver a return on investment—through quantified risk reduction, operational efficiency, or business enablement—its strategic alignment is questionable.
- Overemphasis on Technology: Effective security integrates people, processes, and technology. A partner fixated on tools while dismissing organisational culture and process maturity is a poor strategic fit.
- Vague Communication: An inability to provide clear, concise updates and executive-level reports is a significant liability. Transparency and effective communication are paramount.
A thorough evaluation, focused on both deep technical expertise and genuine strategic alignment, is non-negotiable. To understand how a genuine partnership model functions in practice, review our co-preneurial services. This approach ensures you secure a partner that not only protects your assets but actively contributes to your long-term success.
Guiding Your AI Strategy Securely
The integration of artificial intelligence into core business functions is no longer a question of 'if', but 'how'. For leadership, this presents a dual challenge: seizing the immense opportunities AI offers while mitigating a new class of sophisticated security risks. This is precisely where a high-calibre cyber security consultant demonstrates exceptional value.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
They function as an expert guide, helping you construct a secure foundation for AI innovation from the outset. The objective is to embed a 'secure-by-design' philosophy, ensuring your AI systems are resilient, compliant, and trustworthy from their inception, thereby avoiding costly and brand-damaging security incidents post-deployment.
Navigating New Threats and Regulations
Generative AI offers transformative capabilities but also introduces unique vulnerabilities that traditional IT security frameworks may not address. These are not standard cyber threats; they are more subtle and potentially more damaging.
An experienced consultant can help you understand and neutralise these specific risks:
- Data Poisoning: This occurs when malicious actors intentionally introduce corrupted data into an AI model's training set. The result is a compromised model that produces erroneous outputs, eroding trust in a significant technology investment.
- Sophisticated Phishing Attacks: Adversaries now leverage generative AI to create highly convincing, personalised phishing campaigns at scale, making them far more difficult for employees to detect than traditional, generic attempts.
- Model Inversion and Extraction: This is a form of high-tech intellectual property theft where attackers attempt to reverse-engineer proprietary AI models to extract the sensitive corporate or customer data on which they were trained.
For German enterprises, particularly in regulated sectors like automotive and manufacturing, the challenge extends beyond threats to include stringent compliance requirements. A proficient consultant ensures your AI systems are not only secure but also compliant with standards such as TISAX and ISO 27001, which is essential for maintaining partner trust and market access.
Establishing Robust AI Governance
Effective AI security is not solely about defending against external attacks; it also requires a robust internal governance framework. A consultant can bring critical clarity here, helping to define policies for data access, model usage, and output validation to ensure accuracy and mitigate bias.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
This internal discipline is the foundation of responsible AI deployment. By establishing clear controls and accountability structures, a consultant helps you build systems that are not just powerful, but also transparent and auditable. This provides your teams with the necessary guardrails to innovate safely and effectively.
For a deeper analysis of this topic, our guide to achieving audit-proof enterprise AI security provides a detailed framework for ensuring your AI investments create sustainable value and enhance enterprise resilience.
Moving from Advisor to Strategic Partner
The traditional model for engaging cyber security consultants is becoming obsolete. For years, the relationship has been transactional: an expert is engaged, delivers a comprehensive report with recommendations, and the engagement concludes. While useful, this model places the most challenging burden—implementation and value realisation—squarely on the client.
A paradigm shift is underway, moving from this advisory relationship to a more integrated, strategic partnership. This is not a semantic distinction; it represents a fundamental re-alignment of incentives and objectives. A true partner shares accountability for tangible business outcomes, not just the completion of a statement of work.
The Core of a Co-Preneurial Partnership
This new model redefines the client-consultant dynamic. It is less akin to hiring a contractor and more like onboarding a "co-preneur"—a partner vested in your success. The model is predicated on shared risk and a mutual commitment to achieving measurable goals. For the C-suite, this means you are not just acquiring technical expertise; you are integrating a team focused on measurably reducing risk and actively contributing to your strategic objectives.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
This partnership model is defined by several key principles:
- Shared Accountability: The consultant's success is inextricably linked to your business outcomes, not just the delivery of a presentation deck. They have a vested interest in your success.
- Focus on Production-Ready Solutions: The objective is not theoretical advice but the design and implementation of robust, production-ready security solutions that integrate seamlessly with existing operations.
- Quantifiable Impact: Every initiative is linked to a clear business metric, whether it is reducing the potential financial impact of a breach or accelerating time-to-market by integrating security into the development lifecycle.
The ultimate aim is to engage a partner who operates with the mindset of a stakeholder in your business. They should be as invested in protecting your P&L as you are, ensuring that security expenditures translate directly into a stronger, more competitive enterprise.
Adopting this approach transforms security spending from a cost centre into a strategic investment in future growth and resilience. By selecting cyber security consultants who function as strategic partners, you gain an ally committed not just to identifying problems, but to helping you solve them permanently. It is a more intelligent and effective approach to securing the modern enterprise.
Measuring the ROI of Your Security Investment
Engaging cyber security consultants is a strategic investment that must deliver a clear, quantifiable return. For any executive, this requires moving beyond technical jargon to focus on Key Performance Indicators (KPIs) that directly reflect business resilience and financial performance.
The true measure of success is not the number of vulnerabilities patched, but the demonstrable reduction in business risk.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
This is a critical mindset shift. In Germany, where nearly 60% of companies view cyberattacks as an existential threat—contributing to over €202.5 billion in annual damages—the imperative to justify security spending is intense. This reality has compelled firms to nearly double their cybersecurity allocation from 9% to 18% of their total IT budget. Further analysis of Germany's cybersecurity sector growth on gtai.de is available.

Key Business-Aligned Security KPIs
To demonstrate that technical initiatives are generating strategic value, your consulting partner must report on metrics that resonate in the boardroom. These KPIs establish a direct link between security operations and business stability.
- Mean Time to Resolution (MTTR): This metric measures the average time required to neutralise a security threat from the moment of detection. A consistently decreasing MTTR indicates improving resilience and a reduced window of opportunity for attackers to inflict damage.
- Reduction in Financial Impact: This KPI quantifies the financial benefit of security improvements by tracking the decreasing costs associated with security incidents over time, thereby proving the direct ROI of proactive measures.
- Security Maturity Score: This provides a holistic assessment of your organisation’s defensive capabilities, benchmarked against established frameworks like NIST or ISO 27001. A rising score is a clear indicator of a more robust and defensible enterprise.
Expected Deliverables for Executive Leadership
A strategic partner provides more than raw data; they deliver actionable intelligence that informs high-level decision-making and guides future investment.
The ultimate deliverable is clarity. An effective consultant translates complex technical risk into unambiguous business impact, empowering executives to make informed, strategic decisions about resource allocation and future security investments.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
At a minimum, expect executive summary reports that frame security in the context of business risk and opportunity. A strategic roadmap is also essential—a prioritised plan of security initiatives for the next 12-24 months that is explicitly tied to your company’s core objectives.
This forward-looking approach ensures the engagement remains focused on long-term value creation. For enterprises building in-house AI capabilities, our guide on creating a secure and cost-efficient self-hosted LLM cluster offers a blueprint for a sustainable and secure strategy.
A Few Common Questions
Engaging external cyber security consultants inevitably raises practical questions. The following are common inquiries from leaders in German enterprises, with direct answers to aid your decision-making process.
How Much Should We Budget for a Security Consultant?
The cost of a consulting engagement is contingent upon its scope and objectives. A fixed-price project for a discrete goal, such as a penetration test, differs significantly from an ongoing retainer for long-term strategic guidance.
However, a singular focus on price is a strategic error. The more pertinent analysis is through the lens of value and return on investment (ROI). A premium investment in an expert who materially reduces your risk of a multi-million-euro data breach is a prudent allocation of capital. A low-cost service that merely satisfies a compliance checkbox represents an expense with minimal strategic return.
How Long Does a Typical Engagement Last?
The duration of an engagement is dictated by the strategic objectives. An engagement to prepare for a TISAX audit may be a focused, short-term project of several weeks.
Conversely, retaining a virtual CISO to architect and implement a comprehensive security programme is a long-term strategic partnership that could extend over several years. The key is to align the engagement timeline with specific business objectives and measurable milestones to maintain focus and accountability.
How Do We Make Sure Consultants Work Well with Our Internal Team?
Successful integration hinges on establishing a collaborative partnership, not an adversarial "us vs. them" dynamic. The foundational step is to define crystal-clear roles and responsibilities. All stakeholders—both internal teams and consultants—must have an unambiguous understanding of ownership and accountability to prevent operational friction.
A primary benefit of engaging elite consultants is knowledge transfer. Their role is not merely to perform tasks, but to enhance the capabilities of your internal personnel. They should actively upskill your team, leaving your organisation with a stronger, more self-sufficient security function long after the engagement concludes. The goal is to build lasting institutional strength, not just to fill a temporary resource gap.
At Reruption GmbH, we do not merely consult. We act as co-preneurs, sharing accountability for outcomes and engineering production-ready AI and security systems that deliver tangible business value. Discover our approach.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.