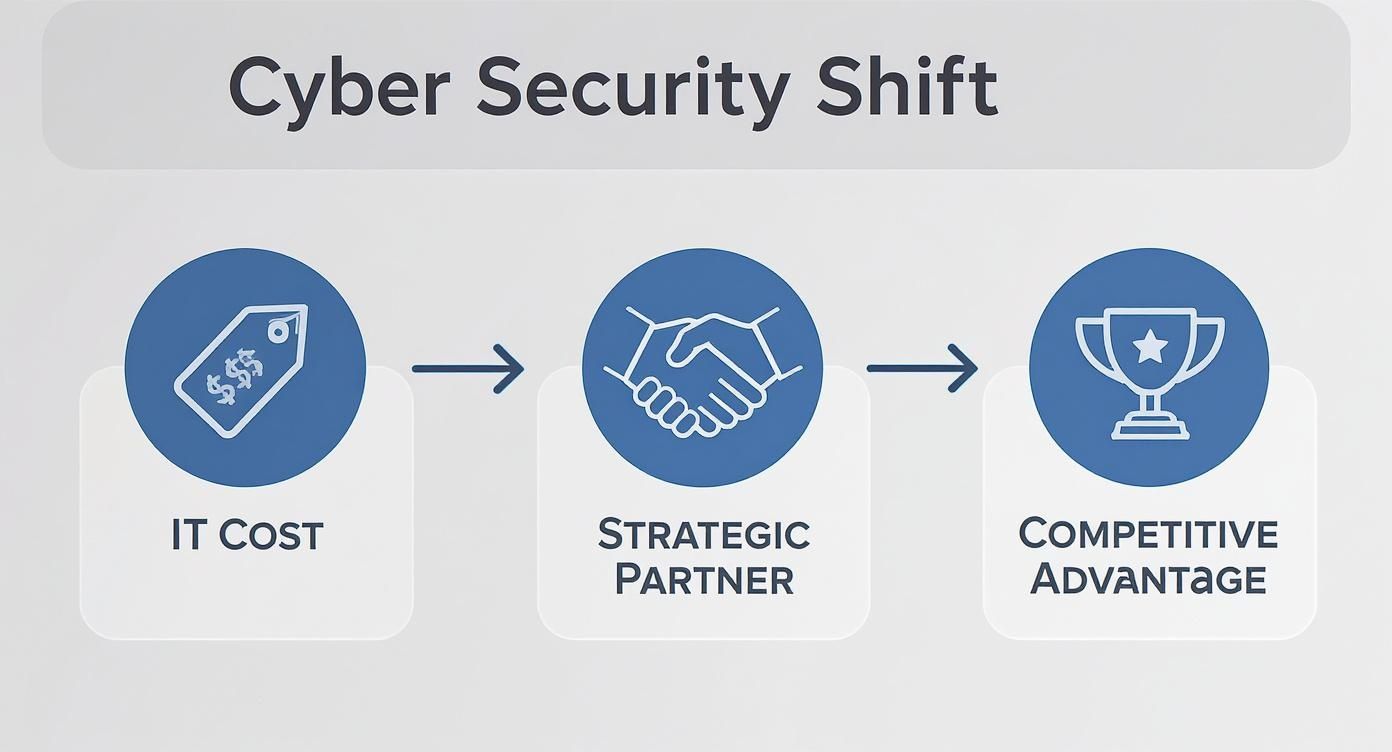
A cyber security consultancy should be viewed not as an IT vendor, but as a strategic partner integral to executive decision-making. Its mandate is to safeguard digital assets, manage enterprise risk, and ensure that security investments directly contribute to business objectives. In the current landscape, a premier consultancy functions as a business enabler, providing the strategic confidence required for innovation—particularly with artificial intelligence—without exposing the organisation to unacceptable risk.
Why a Cyber Security Consultancy is Non-Negotiable for Modern Enterprises

In today's competitive economy, stasis is not a viable strategy. Innovation is the primary differentiator between market leaders and followers. For German enterprises, particularly within core sectors such as automotive and manufacturing, the adoption of AI and machine learning presents a significant opportunity for value creation. However, this opportunity is accompanied by complex, often latent, security risks that demand executive attention.
The traditional, reactive security posture—addressing vulnerabilities only after an incident—is no longer defensible. The sophistication of modern threats necessitates a proactive framework where security is integrated into corporate strategy from inception. It is precisely within this paradigm that a high-calibre cyber security consultancy demonstrates its strategic value.
Transitioning Security from a Cost Centre to a Strategic Enabler
Historically, cyber security was relegated to a cost centre within the IT department, disconnected from boardroom strategy. This perspective is now dangerously obsolete. A strategic consultancy reframes security as an active enabler of business objectives, transforming it from a defensive shield into a competitive advantage.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
This partnership is cultivated at the executive level, defined by shared accountability for business outcomes. The strategic dialogue evolves beyond "preventing breaches" to the systematic de-risking of innovation itself.
In practical terms, this strategic alignment empowers an organisation to:
- Accelerate the launch of new digital products and AI-driven services by embedding security as a seamless component, not a final bottleneck.
- Strengthen customer trust and brand equity by demonstrating a robust commitment to data protection.
- Secure critical supply chains, meeting stringent compliance mandates such as TISAX.
- Safeguard high-value intellectual property during the development of next-generation technologies.
The objective is not merely to protect existing assets, but to create a secure foundation for future growth. A strategic partner ensures that security capabilities scale in lockstep with corporate ambition, providing the resilience required for bold market manoeuvres.
To align security initiatives with business goals, it is essential to map specific services to the objectives they support. The following table provides a high-level overview of this connection.
Core Service Pillars of a Strategic Cyber Security Partner
| Service Pillar | Strategic Business Objective |
|---|---|
| Risk Assessments & Strategy | De-risk innovation and investment by identifying and quantifying threats before they impact strategic initiatives. |
| Secure Architecture & DevSecOps | Accelerate time-to-market for new products by integrating security throughout the development lifecycle. |
| Compliance & Certifications (ISO, TISAX) | Unlock new revenue streams and strategic partnerships by meeting non-negotiable industry and supply chain requirements. |
| Incident Response & Resilience Planning | Protect brand reputation and ensure business continuity by preparing the organisation to effectively manage a crisis. |
| Security Audits & Penetration Testing | Build and maintain stakeholder trust by validating security controls and demonstrating a proactive defence posture. |
| AI/ML Security Integration | Enable safe innovation with emerging technologies by protecting models, data, and algorithms from unique AI-specific threats. |
This framework illustrates how technical security functions translate directly into tangible business advantages, transforming a traditional cost centre into a powerful engine for growth.
Navigating a High-Stakes Environment
The data for Germany paints a stark picture. In 2024, the German cybersecurity market reached USD 12.5 billion and is projected to exceed USD 30 billion by 2035. More soberingly, 65% of German companies now consider cyberattacks an existential threat. The financial toll is staggering, with damages reaching EUR 178.6 billion in the last year alone.
In this high-stakes environment, even the most capable in-house teams cannot be expected to operate in isolation. Expert guidance from experienced cyber security consultants is no longer a discretionary expense—it is a critical investment in future growth, corporate resilience, and the ability to convert ambitious strategy into market reality.
The Mandate of a Top-Tier Cyber Security Consultancy
Engaging a premier cyber security consultancy is not akin to procuring software or hiring a contractor. It is an investment in strategic capability. These partners do not merely sell tools or bill hours; their objective is to deliver tangible business outcomes by translating complex technical challenges into clear, strategic actions that protect revenue, reputation, and competitive positioning.
The most effective consultancies begin with a deep immersion into the client's industry, whether automotive, manufacturing, or finance. This sector-specific fluency is paramount. In Germany, the market has already demonstrated a clear preference for expert services over product sales. While security solutions constitute a USD 9.3 billion market in 2024, it is the services segment that exhibits the fastest growth. This indicates a clear executive demand for hands-on expertise in audits, compliance roadmaps, and strategic guidance.
Strategic Risk Assessments
A cornerstone of any reputable consultancy is the strategic risk assessment. This is not a standard vulnerability scan that generates a voluminous list of technical issues. It is a business-centric analysis that links potential security weaknesses to concrete operational and financial risks, articulated in a language the board understands.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
Consider it a strategic audit of the entire digital enterprise. The consultancy examines technology, processes, and personnel to address critical questions:
- Where are our most valuable digital assets—our "crown jewels"?
- What specific threat scenarios could disrupt core business operations or lead to the exfiltration of intellectual property?
- What is the quantifiable financial impact if our new AI-driven production line is compromised?
The deliverable is not a dense technical report, but a clear, prioritised roadmap. It provides executives with the data required to make informed investment decisions, allocating resources where they will have the most significant impact on reducing business risk.
Secure by Design for AI Innovation
As organisations accelerate the integration of AI and machine learning, they inadvertently create new attack surfaces. A top-tier consultancy introduces a Secure by Design methodology. This framework mandates that security is not a final-stage validation, but a foundational principle integrated into the innovation process from the initial concept workshop.
This forward-thinking approach ensures that AI initiatives are built on a resilient foundation. It encompasses designing secure data pipelines, protecting valuable models from theft or manipulation, and ensuring customer-facing applications are both intelligent and trustworthy. By embedding security from day one, organisations avoid costly post-deployment remediation and can bring new AI-powered services to market with greater speed and confidence.
Mastering Compliance and Certification
Navigating Germany's complex regulatory landscape, particularly within intricate supply chains, presents a formidable challenge. Expert consultancies possess mastery of critical frameworks such as TISAX for the automotive sector and ISO 27001 for information security management.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
Their role extends beyond audit preparation. They architect a robust, sustainable security posture where compliance with stringent standards becomes an organic outcome of daily operations. This transforms compliance from a costly obligation into a competitive differentiator, unlocking access to key markets and partners.
These core offerings represent only the foundation. To fully appreciate the defensive capabilities a consultancy provides, it is valuable to understand tactical validations like What is penetration testing?, which simulates a real-world attack to assess defensive efficacy. A holistic view of all cyber security services available reveals how discrete components integrate to enhance overall business resilience. Ultimately, these services work in concert to build a security program that is not merely compliant, but demonstrably effective.
How To Select The Right Security Partner For Your Business
Selecting a cyber security consultancy is a strategic decision, not a procurement exercise. This choice will directly influence your organisation's ability to innovate securely, maintain a competitive edge, and effectively navigate a security incident.
A successful partnership results in a genuine extension of your leadership team. A misaligned choice leads to expensive missteps and exposes the business to significant risk.
Therefore, the selection process must penetrate beyond polished presentations. For German organisations, particularly in the automotive and manufacturing sectors, this is paramount. You require a partner who understands the nuances of your operating environment—from the complexities of TISAX compliance across global supply chains to the unique challenges of securing proprietary AI models.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
The objective is to identify a partner demonstrating clear strategic alignment. Seek evidence that they can connect security initiatives to business objectives, offer transparent and flexible engagement models, and are committed to enhancing your team's capabilities, rather than fostering dependency.
The Litmus Test: Do They Understand Your Business?
The first and most critical evaluation criterion is this: can the potential consultancy articulate its value in business terms, or is its language confined to technical jargon?
A tactical vendor will focus on firewalls, endpoints, and vulnerability metrics. A true strategic partner will initiate the conversation by inquiring about revenue targets, market expansion plans, and the innovation pipeline.
Their initial discovery should probe the core mechanics of your business. They should seek to understand the precise financial impact of a disruption to a specific production line or how a data breach could erode the trust of key clients. This business-first methodology is the clearest indicator that their guidance will be grounded in commercial reality.
Critical Questions To Ask Your Potential Partner
To move beyond superficial sales claims, your evaluation team must be equipped with incisive, strategically focused questions. The goal is to assess the depth of their methodology and strategic acumen, particularly concerning emerging challenges like AI security and complex compliance frameworks.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
Incorporate these essential questions into your evaluation process:
- On Strategic Alignment: "Provide a specific example where you translated a technical risk assessment into a compelling business case for a C-level audience within our industry."
- On AI & Innovation: "Detail your methodology for securing a new AI or machine learning application, from data ingestion through to model deployment and monitoring."
- On Compliance Mastery: "Describe your approach to guiding a company through TISAX or ISO 27001 certification. How do you ensure the implemented controls are sustainable and operationally efficient?"
- On Knowledge Transfer: "How will you actively enhance the capabilities of our internal teams during this engagement? What specific mechanisms do you employ to ensure we are more self-sufficient upon conclusion?"
The purpose of these questions is to determine if they operate as a genuine partner. An exceptional partner does not create dependency; they build the organisation's long-term resilience and institutional knowledge. Explore how a consultancy can assist by reviewing our in-depth articles on strategic risk management and compliance.
To clarify where your organisation might require support, the following decision tree outlines the primary value-delivery pathways of a consultancy. It helps determine whether the most pressing need is risk identification, secure system development, or compliance attainment.
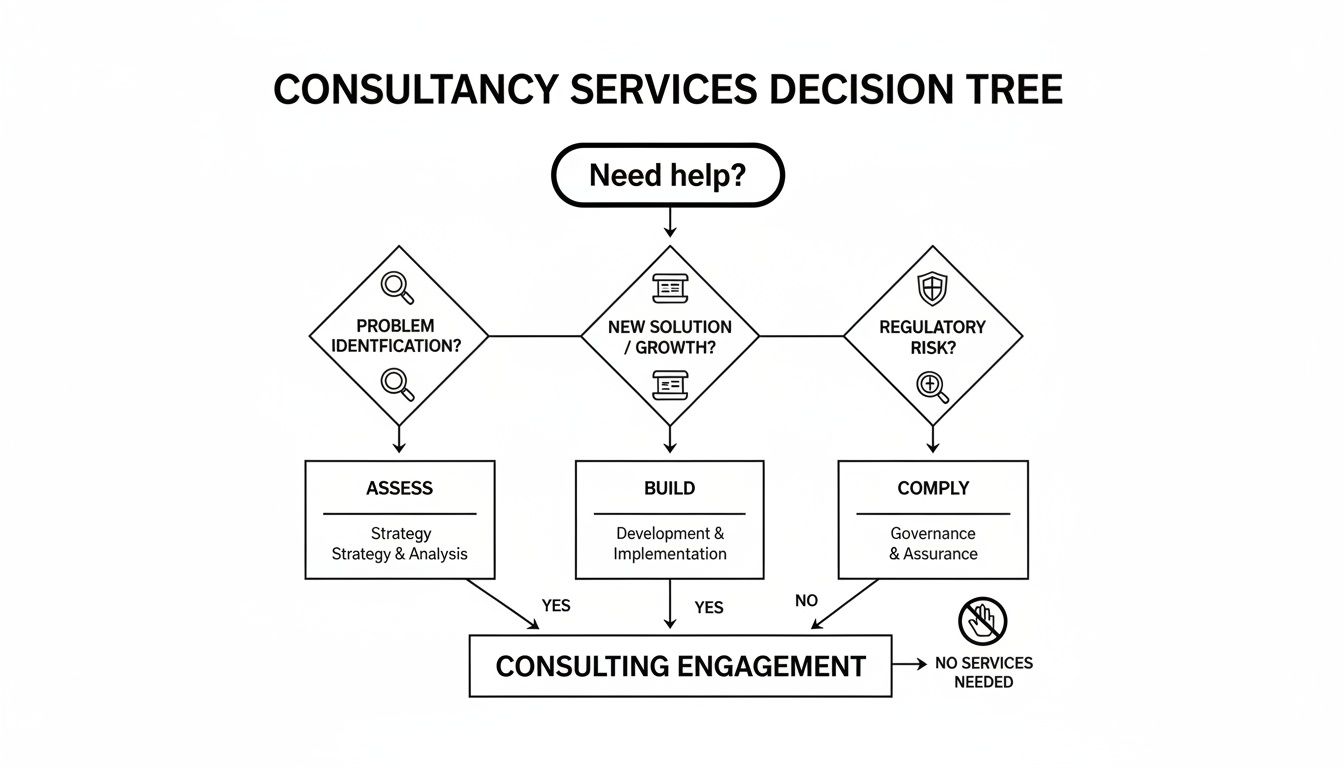
As the diagram illustrates, the optimal starting point is always the core business problem you aim to solve. This ensures that all efforts are focused on tangible outcomes from the outset.
Integrating Security into Your AI and ML Innovations
Artificial Intelligence and Machine Learning are not merely technological advancements; for German industry, they represent a fundamental paradigm shift. These technologies are poised to redefine manufacturing efficiency, enable hyper-personalised customer experiences, and unlock novel revenue streams. However, this progress introduces a new class of complex security challenges for which traditional security models are ill-equipped.
The critical takeaway for leadership is unequivocal: security cannot be a post-deployment consideration. It must be an integral component from the initial line of code and the first strategic meeting.
This is not a directive to decelerate innovation. On the contrary, it is about building the strategic confidence to move faster. An expert cyber security consultancy does not function as a final-stage auditor; they act as a co-creator, embedding resilience into the project's foundational DNA. This ensures that your AI ventures are not only powerful but also trustworthy and market-ready.
Protecting the Engine of AI: The Data Pipeline
An AI model can be conceptualised as a high-performance engine, with data as its fuel. If this fuel is compromised at any point—during collection, processing, or training—the engine will malfunction, produce flawed results, and potentially cause significant operational damage. The integrity of the data pipeline is therefore paramount.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
To implement this, you can establish an unbroken chain of custody for your data. This extends far beyond basic encryption. It involves implementing rigorous access controls, continuous monitoring, and data validation protocols to ensure data integrity. The objective is to guarantee that the data feeding your models is authentic, accurate, and untampered with, thus preventing skewed outcomes that could lead to detrimental business decisions. A consultancy helps implement this.
Defending the Model Itself
A trained machine learning model is more than a tool; it is a high-value piece of intellectual property and a core business asset. These models, however, are susceptible to unique attacks that can completely undermine their integrity and value.
An AI model is not a static piece of software; it is a dynamic system that can be manipulated. Attackers can attempt to poison the training data to create hidden backdoors, or they can reverse-engineer a deployed model to steal the proprietary algorithms that give you a competitive edge.
Securing the model requires a multi-layered defence strategy. This includes advanced techniques such as adversarial training, where the model is deliberately exposed to manipulated data to enhance its resilience. It also involves continuous monitoring to detect anomalous behaviour indicative of an attack. A specialised consultant provides the expertise to implement these safeguards, protecting your investment and ensuring the model performs precisely as intended.
Deploying LLMs and Generative AI Securely
The proliferation of Large Language Models (LLMs) presents immense opportunities for copilots, automated communications, and insight generation. However, connecting a powerful LLM directly to sensitive internal corporate data without robust controls is a direct path to data leakage and significant compliance penalties.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
To implement secure deployment, you can design a secure "wrapper" or governance layer around these models. This typically involves:
- Robust Input and Output Filtering: This prevents malicious prompts from manipulating the model and, critically, blocks sensitive information from being included in its responses.
- Airtight Access Control: You can define precisely which users can query the model on which topics, and which data sources it is permitted to access based on a user's role and permissions.
- Compliance by Design: Your application must be architected from the ground up to adhere to GDPR and other data protection regulations—a non-negotiable requirement for operating in the German and EU markets.
By integrating these controls, you can harness the transformative power of LLMs without exposing the organisation to unacceptable levels of risk. For a detailed examination of this specialised domain, you can seek professional guidance on AI security and compliance.
Ultimately, this proactive methodology transforms security from a barrier into a potent enabler, providing the freedom to innovate boldly and securely in the age of AI.
Measuring the Real-World Impact of Your Security Investment
While strategy provides direction, the boardroom's primary currency is measurable results. Any top-tier cyber security consultancy understands this imperative. Its function is to translate complex security initiatives into tangible business outcomes.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
The definitive proof of a successful partnership is not found within a technical report laden with jargon. It is demonstrated through real-world achievements that directly advance the company's strategic objectives. This requires moving beyond abstract metrics like "vulnerabilities patched" to focus on key performance indicators (KPIs) that resonate with the C-suite: quantified risk reduction, accelerated time-to-market, and a clear return on security investment (ROSI).
From Compliance Burden to Commercial Advantage
Consider a classic scenario: a German automotive supplier must secure a major contract with an OEM, contingent upon achieving TISAX certification. A traditional perspective views this as a costly compliance hurdle. A strategic approach, guided by an expert consultancy, reframes it as a powerful commercial enabler.
In this context, the engagement is not merely about passing an audit. It is about architecting a robust information security management system (ISMS) that genuinely protects sensitive prototype data and fortifies the entire supply chain.
Success is then measured by metrics that impact the business:
- Time-to-Certification: How rapidly did the company achieve the required TISAX Assessment Level (e.g., AL3)? Each day saved accelerates the timeline to revenue generation.
- Quantified Risk Reduction: Can the engagement demonstrate a measurable reduction in the risk of intellectual property theft, expressed in financial terms?
- Contractual Wins: The ultimate KPI. Did the company secure the multi-year contract that was previously at risk due to compliance gaps?
Enabling Secure Innovation in AI
Another powerful example involves an e-commerce platform launching a new AI-powered personalisation engine to increase customer engagement and sales. This project introduces significant risks related to customer data privacy and the integrity of the AI model.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
A consultancy partner operating in a co-preneurial capacity does not merely identify problems; they integrate with the innovation team to embed security from the project's inception. Security thus becomes an accelerator, not an inhibitor. The consultant helps design a secure architecture that meets stringent GDPR requirements while enabling the AI to function optimally.
The impact is demonstrated through metrics that connect security directly to business performance. This includes the successful and on-schedule launch of the new feature without security incidents, alongside a documented increase in customer trust and a reduction in cart abandonment rates.
This clear linkage between robust security and positive business outcomes is fuelling significant market growth. Germany's cybersecurity market is projected to grow from USD 14.02 billion in 2025 to USD 23.89 billion by 2030. The transportation sector leads this expansion with a 19.7% CAGR, underscoring the critical importance of secure innovation to Germany’s core industries.
Tracking the Metrics That Matter
Ultimately, the value of a strategic security partner is substantiated by data. By establishing a clear baseline and relentlessly tracking progress against business-focused KPIs, you can construct an undeniable case for continued investment. For further information on transforming security data into actionable business intelligence, review our guide on analytics and insights.
The right partner makes it possible to demonstrate not just how you are protecting the business, but how you are actively enabling its growth.
Your Path to Secure and Lasting Innovation
In an era of rapid technological advancement, the conversation around cyber security must evolve. It is no longer sufficient to focus on perimeter defence and threat reaction. Security must be positioned as a foundational pillar of business success, particularly with the enterprise-wide adoption of artificial intelligence. This is not an IT-level discussion; it is a leadership imperative.
Engaging a cyber security consultancy is not a procurement decision for a commodity service; it is the formation of a strategic business alliance. It is a choice to partner with experts who can transcend technical jargon and articulate risk in terms of its impact on the bottom line. This partnership provides the executive confidence to pursue ambitious goals, knowing that innovation is not outpacing the ability to protect what has been built.
More Than a Shield—It's a Strategic Edge
The primary objective is to transition security from a defensive cost centre into a proactive, competitive advantage. A true strategic partner does not simply remediate vulnerabilities; they help embed resilience into the corporate DNA and product lifecycle. They ensure the organisation is prepared not only for today's threats but also for the challenges—and opportunities—of tomorrow.
This forward-thinking approach enables your business to:
- Innovate Fearlessly: Develop and launch new AI-powered services with the confidence that they are secure and compliant from the conceptual stage.
- Build Enduring Trust: Demonstrate to all stakeholders—customers, partners, and regulators—a serious commitment to data protection, thereby building lasting relationships.
- Grow Sustainably: Establish a solid operational foundation where new technology creates long-term value rather than introducing new liabilities and operational friction.
The selection of a partner is about finding a shared vision. You require a firm that operates less like a supplier and more like a co-preneur—one that is genuinely invested in your business outcomes and success.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
Your Next Steps on the Journey
The path forward begins with an objective assessment of your current posture. This requires asking critical questions about your readiness to innovate securely. Where are your greatest vulnerabilities? How can you integrate security into your product development lifecycle from day one? Does your team possess the requisite skills to address the unique security challenges presented by AI?
The right partner will collaborate with you to navigate this process, mapping out a clear, pragmatic plan. They will work shoulder-to-shoulder with your teams to transform strategic concepts into secure, market-leading products. This is not a prescriptive engagement; it is a collaborative effort that makes security an intrinsic part of your corporate culture. It is how you prepare to seize the future—protected from its risks and positioned for its rewards. The journey begins with finding a partner who shares your vision.
Your Questions Answered
For leaders considering a strategic security partner, several key questions typically arise. Here are direct answers to the most common inquiries from a business perspective.
Consultancy vs. MSSP: What's the Real Difference?
A Managed Security Service Provider (MSSP) functions as your operational security team. They manage day-to-day security tasks: monitoring firewall alerts, managing endpoint detection and response, and ensuring the operational continuity of security controls. Their role is essential but is fundamentally operational.
A cyber security consultancy operates at the strategic level. The focus is not on managing systems, but on shaping strategy to ensure security is woven into core business objectives.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
Our mandate includes:
- Architecting a security roadmap that directly supports business growth initiatives.
- Executing risk assessments that quantify threats in terms of financial and operational impact.
- Navigating the complexities of compliance frameworks like TISAX.
- Designing the secure architecture for next-generation innovations, particularly those involving AI.
Analogy: A consultancy is the architect who designs the secure blueprint for the enterprise. The MSSP is the expert team that manages the security systems within the completed structure.
How Should I Budget for This?
Budgeting for a high-level consultancy should be viewed as a strategic investment in corporate resilience and growth capability, not as an operational cost. The final investment will depend on the scope and complexity of the defined objectives.
Engagements typically fall into two models:
- Project-Based: For a defined outcome, such as a TISAX readiness assessment or the security architecture design for a new AI platform.
- Retainer-Based: For continuous, CISO-level advisory. This provides ongoing strategic guidance and oversight for the entire security programme.
A modern, business-aligned approach ties payment to the achievement of specific milestones and measurable business outcomes. The central focus should always be on the value and quantifiable risk reduction delivered, not simply the hourly rate of the consultants. This ensures complete alignment with your objectives.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
When Do We Bring a Consultancy into Our AI Projects?
The concise answer is: at the very beginning. The ideal time is during the initial strategy and discovery phase, before a single line of code has been written.
Attempting to "bolt on" security after development is not merely inefficient; it is financially imprudent. Remediating a security flaw post-launch can be up to 100 times more costly than addressing it during the design phase.
By engaging a partner early, you build on a secure foundation from day one. We can assist your team in mapping out secure data governance, selecting a technology stack that meets both security and compliance requirements, and integrating security into the development lifecycle (DevSecOps). This proactive approach prevents costly rework, mitigates the risk of show-stopping vulnerabilities, and ensures your innovation is both powerful and protected from its inception.
At Reruption, we do not just advise. We partner with you as co-preneurs to turn ambitious ideas into secure, market-leading innovations. Discover our approach at https://www.reruption.com.