In an era of accelerated AI adoption, the role of the modern cyber security consultant has fundamentally evolved. They are no longer mere technical auditors; for German enterprises, they are indispensable strategic partners. Their mandate is to align security frameworks with executive-level objectives, ensuring that innovation proceeds without being constrained by unacceptable risk.
The Cyber Security Consultant as a Strategic Business Enabler

The function of a cyber security consultant has transcended reactive damage control and compliance. Today, these experts enable business growth, particularly as German companies integrate complex AI technologies. Their principal value lies in transforming security from a mandatory expenditure into a distinct competitive advantage.
Rather than applying security measures retrospectively, a forward-thinking consultant integrates security into the innovation lifecycle from its inception. This "security by design" methodology is critical for high-stakes AI initiatives, such as the deployment of Large Language Models (LLMs) or the construction of automated data analytics pipelines.
The Consultant as a Co-Preneur
The most effective cyber security consultants function as a 'Co-Preneur'—a strategic partner who assumes shared accountability for business outcomes. They navigate leadership through the intricate and often opaque threat landscape associated with AI, ensuring that new technologies are not only powerful but also secure and compliant from day one.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
A consultant's value is not measured solely by the vulnerabilities they identify, but by the secure innovation they enable. They establish the strategic guardrails that allow ambitious concepts to become resilient, market-ready realities.
This partnership model is instrumental for complying with stringent regulations like NIS2 while pursuing aggressive growth targets. To better understand how these experts function as strategic allies, consider the insights from an experienced cybersecurity advisor.
In essence, a premier consultant ensures an organisation's most significant initiatives are built upon a foundation of resilience. This strategic alignment is what transforms concepts into tangible, secure assets. For a more exhaustive analysis, our detailed overview of cyber security consultants and their evolving role offers further insights.
To clarify this paradigm shift, the following table outlines the structure of a modern engagement and its strategic value.
Modern Cyber Security Consultant Engagement Framework
| Area of Engagement | Core Function | Strategic Value for Management |
|---|---|---|
| AI & Innovation Security | Integrates robust security protocols throughout the AI development lifecycle. | Facilitates the secure adoption of emerging technologies, converting security into a competitive differentiator. |
| Regulatory Compliance (NIS2, etc.) | Translates complex legal mandates into actionable, verifiable security controls. | Mitigates legal and financial risk, ensuring business continuity and unimpeded market access. |
| C-Level Strategy Alignment | Serves as the crucial liaison between technical implementation teams and executive leadership. | Guarantees that security investments directly support and safeguard core business objectives. |
| Threat Landscape Analysis | Delivers proactive intelligence on emerging threats pertinent to the business and its sector. | Enables leadership to make informed, risk-based decisions on capital and resource allocation. |
Ultimately, this collaborative model elevates security from a reactive, technical function to a proactive, strategic capability that both protects and drives business growth.
Understanding Germany’s Unique Cybersecurity Landscape

Germany’s industrial core—its renowned Mittelstand and corporate leaders—operates within a highly demanding environment. The nation's cybersecurity climate is defined by the convergence of rapid market expansion, a persistent shortage of skilled experts, and a notably complex regulatory framework. For any executive tasked with driving innovation while ensuring enterprise security, mastering these dynamics is a strategic imperative.
The demand for robust security is intensifying. The German cybersecurity market is projected to more than double, expanding from USD 11.78 billion to USD 25.91 billion by 2034. This exponential growth underscores Germany's significant position, commanding 19.10% of Europe's cybersecurity consulting market. A deeper quantitative analysis is available in this market analysis of Germany's cybersecurity sector growth on duscons.com.
This demand, however, is constrained by a critical skills deficit. With thousands of unfilled IT security positions nationwide, internal teams are operating at maximum capacity. They are often consumed by daily operational issues, leaving little bandwidth to address the specialised security requirements of new AI initiatives. This talent gap makes engaging an external cyber security consultant a strategic necessity rather than a discretionary choice.
Navigating the Regulatory Maze
In addition to market pressures, German enterprises must navigate a complex web of compliance mandates. These are not mere guidelines but rigid requirements that carry substantial financial and reputational risk.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
Key regulations include:
- General Data Protection Regulation (GDPR): The cornerstone of data privacy, prescribing strict controls for handling the personal data of EU citizens.
- NIS2 Directive: An EU-wide mandate elevating security standards for critical infrastructure, requiring rigorous risk management and prompt incident reporting.
- TISAX (Trusted Information Security Assessment Exchange): A mandatory standard for the automotive industry, requiring all supply chain partners to demonstrate verifiable security maturity.
Non-compliance can result in significant fines, loss of contracts, and long-term brand damage. An expert consultant provides the focused expertise required to navigate this complexity and implement effective, compliant solutions.
For German leadership, cybersecurity is not merely a technical issue—it is a core business challenge. Amid market expansion, talent scarcity, and regulatory scrutiny, inaction represents the greatest risk.
Engaging a consultant is the most efficient method to address internal skills gaps. It provides immediate access to a specialist with deep expertise in TISAX, NIS2 audit preparation, and ensuring new AI initiatives are GDPR-compliant by design. We address many of these topics in our articles on IT security in Germany. This proactive approach transforms compliance from an operational burden into a competitive advantage, solidifying your market position.
Securing Your AI Revolution: A Strategic Imperative
As German enterprises integrate AI into their core operations, they unlock significant efficiencies while simultaneously creating new vectors for cyber threats. The rapid pace of AI adoption often results in security being addressed retrospectively, exposing high-value data and critical systems. For executive leadership, managing these emergent risks is a strategic necessity.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
The vulnerabilities associated with AI differ fundamentally from traditional IT threats. Systems such as Large Language Models (LLMs), copilots, and AI-driven data pipelines introduce unique attack surfaces that standard security protocols may fail to address. These are not abstract concerns; they represent clear and immediate dangers to corporate data, reputation, and competitive positioning.
Deconstructing AI-Specific Threats
To construct a resilient AI strategy, it is essential to move beyond technical jargon and understand the concrete risks. This is where a skilled cyber security consultant provides critical value, demystifying these threats and translating them into tangible business risks.
Key vulnerabilities include:
- Prompt Injection Attacks: This involves manipulating LLM inputs to bypass safety filters, compelling the model to disclose sensitive information or execute unauthorised commands.
- Data Poisoning: Malicious actors intentionally corrupt the training data used by an AI model. This can degrade the model's accuracy or embed hidden biases, leading to flawed business decisions.
- Model Evasion: Adversaries craft specific inputs designed to deceive an AI model into making an incorrect classification, potentially compromising security systems that rely on AI for threat detection.
These threats highlight a critical capability gap: traditional security teams may lack the specialised expertise to secure AI systems effectively. A strategic consultant delivers immense value in closing this gap.
A consultant's objective is not to impede AI projects but to build a secure foundation that enables safe acceleration, transforming AI from a potential liability into a strategic asset.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
An expert consultant assists in developing a robust AI governance framework from the outset. This entails implementing secure deployment practices, defining stringent data governance protocols, and conducting specialised audits tailored to AI vulnerabilities. To protect the most critical assets within your AI initiatives, implementing strong defences like immutable backup solutions for ransomware defense is essential.
By integrating security into every phase of the AI lifecycle, a consultant ensures that innovation strengthens—rather than weakens—your organisation's overall security posture. For a more detailed examination of this process, please refer to our complete 2025 guide to building audit-proof AI systems.
How to Select the Right Security Partner
Selecting a cyber security consultant is a high-stakes leadership decision, more akin to choosing a joint venture partner than procuring a vendor. You are not merely purchasing a service; you are integrating a strategic ally—a 'Co-Preneur'—who shares accountability for the business outcome. This requires a rigorous evaluation process that extends beyond technical certifications to assess their ability to drive secure innovation within your organisation.
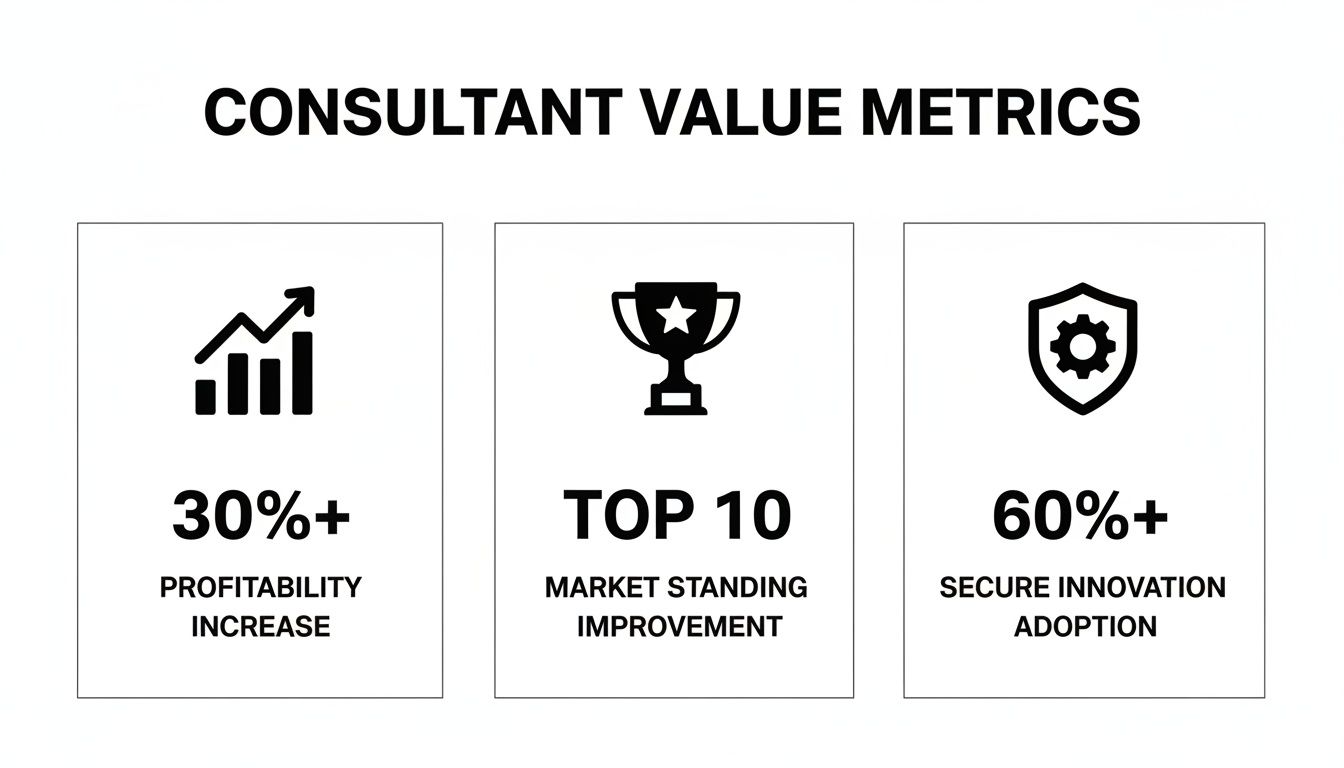
The dynamics of the German market amplify the importance of this decision. Germany represents 19.10% of Europe's cybersecurity consulting market, a sector that has grown by 52.15% since 2021. This expansion is driven by new regulations like NIS2 and a significant skills gap, with over 100,000 unfilled IT roles. Consequently, companies are increasingly seeking external expertise, especially for securing AI. For an innovation leader, the right partner can reduce deployment risks and improve resilience by an estimated 45%. Additional data on this trend is available in the full cybersecurity consulting market report.
Core Criteria for Evaluating Consultants
A first-rate consultant possesses not only technical knowledge but also contextual intelligence. Your evaluation framework must balance their technical expertise with a deep understanding of your industry and a proven methodology for de-risking complex projects.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
Essential criteria include:
- Deep Industry Experience: Do they understand the unique operational and regulatory challenges of your sector, such as TISAX in automotive or data handling regulations in manufacturing? A generic security plan is insufficient.
- A Proven De-Risking Methodology: Request a detailed outline of their framework for identifying, quantifying, and mitigating risks in AI projects. A genuine partner will present a clear, methodical process, not just a list of software tools.
- German Regulatory Fluency: Comprehensive knowledge of GDPR, NIS2, and other local regulations is non-negotiable for building compliant systems from inception.
- Cultural and Strategic Fit: The consultant must function as an extension of your leadership team, capable of translating complex technical risks into clear business language for executive decision-making.
The diagram below illustrates the layered approach to AI security, from high-level governance to specific threat mitigation.
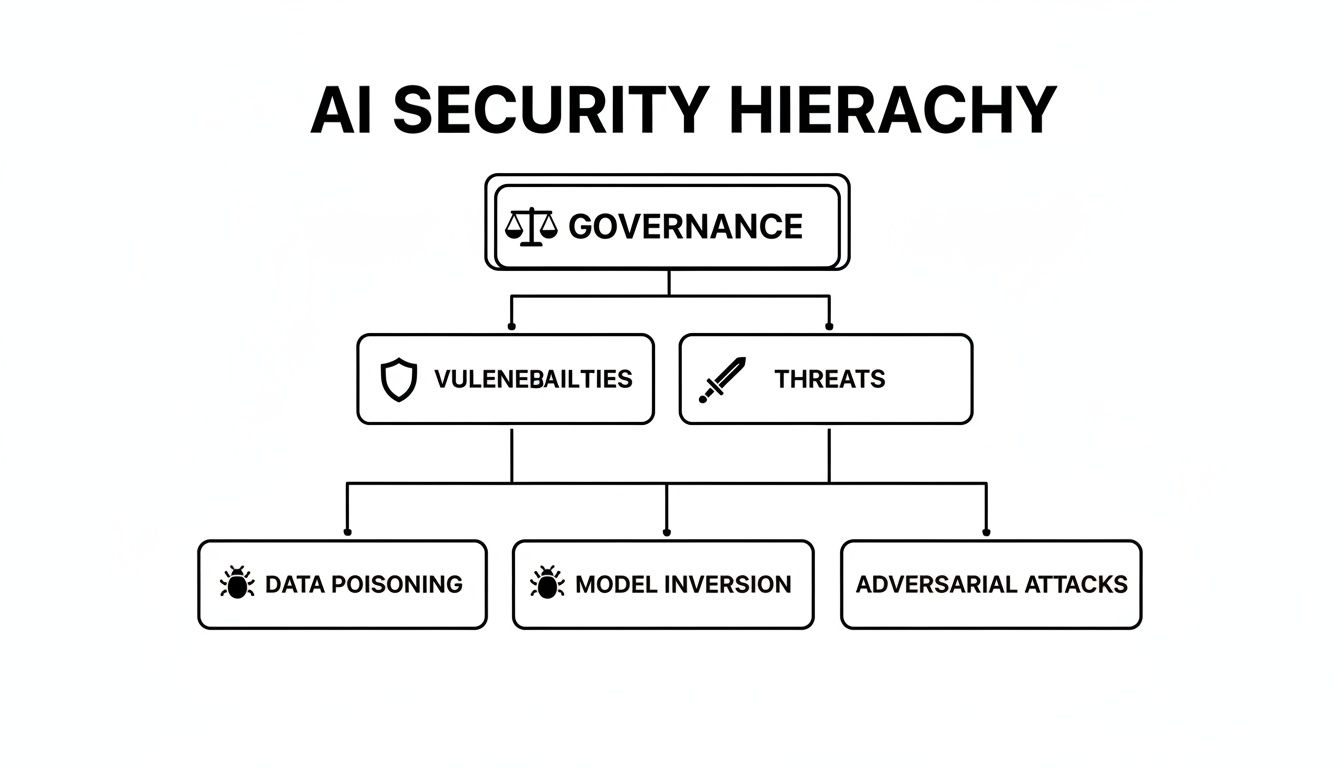
As depicted, robust AI security begins with a strong governance framework. This foundation dictates the approach to all other elements, from system vulnerabilities to tactical threats.
Insightful Interview Questions to Ask
Move beyond standard interview scripts to probe a consultant's real-world problem-solving capabilities and strategic acumen. These questions are designed to reveal how they think, not merely what they know.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
How would you align our AI security roadmap with our primary business objective of increasing market share by 15% over the next two years?
This question shifts the focus from a purely technical discussion to a strategic one, immediately revealing their ability to connect security initiatives with commercial objectives.
- Describe an instance where a client's project goals conflicted with security best practices. How did you navigate this to achieve a secure and successful outcome?
- Walk us through your process for threat modelling a new generative AI application that will handle sensitive customer data.
- Imagine you discover a critical vulnerability one week before a major product launch. What is your immediate three-step action plan for leadership?
These questions serve as a pressure test, revealing a consultant's pragmatism, communication skills, and ability to perform under pressure. Their responses will provide a clear indication of whether you are engaging a strategic partner or simply a service provider. For further reading, we have also detailed what is required to effectively manage risk management and compliance in your organisation.
Building a Business Case for Security Investment
For any C-suite executive, a significant expenditure requires a clear return. Securing a top-tier cyber security consultant is no exception. The key is to frame the discussion not around abstract threats, but with a pragmatic, data-driven business case.
This is not an insurance policy; it is an investment with measurable dividends. The value proposition is based on three pillars: risk reduction, operational efficiency, and innovation enablement. Articulating the investment in these terms provides leadership with the financial clarity needed for a sound decision.
Quantifying the Return on Investment
Calculating the ROI involves a straightforward cost-benefit analysis, weighing the investment against the significant potential costs of inaction. This requires a rigorous assessment of the financial, operational, and reputational risks.
Germany's IT Security Services market has grown to €4.5 billion, expanding at a 5.8% CAGR since 2020. This growth is driven by a severe talent shortage colliding with escalating threats. With 85% of companies reporting project delays due to this gap, the value of external expertise becomes unequivocally clear. More details are available in this report on the German IT security services market on ibisworld.com.
When constructing the financial model, consider these factors:
- Cost of a Potential Breach: This includes direct financial losses, substantial regulatory fines (under GDPR or NIS2), and the significant costs of incident response and recovery.
- Operational Efficiency Gains: An effective consultant streamlines processes, alleviating the workload on internal teams, particularly in compliance-related tasks. They fill critical skill gaps and accelerate project timelines.
- Innovation Enablement: Calculate the opportunity cost of an AI project delayed or shelved due to security concerns. A consultant de-risks these strategic initiatives, enabling faster, safer market entry.
The most compelling business case for a cyber security consultant frames security not as a cost centre, but as a direct enabler of core business goals: protecting revenue, optimising operations, and fuelling growth.
This approach elevates the conversation from a technical security review to a strategic financial discussion. To further refine this strategy, our guide on the role of a consultant in business intelligence may also prove valuable.
Frequently Asked Questions
We frequently receive questions from management teams evaluating the engagement of a cyber security consultant. Here are direct answers to the most common inquiries.
What is the primary role of a consultant on an AI project?
The consultant functions as a strategic partner, not merely a technical expert. Their primary role is to embed security into the core design of your AI project from its inception. This extends far beyond routine vulnerability remediation.
They are responsible for establishing robust AI governance frameworks, safeguarding data privacy, and addressing model vulnerabilities proactively. Critically, they possess deep knowledge of the German regulatory landscape—including GDPR and NIS2—enabling secure innovation while ensuring compliance.
How can we measure the ROI of this engagement?
The return on investment is measured by tangible risk reduction. A primary metric is the comparison of a potential data breach's cost—which can be substantial—against the consultant's fees.
However, the value extends further. A skilled consultant can accelerate time-to-market by supplementing internal skill gaps. By ensuring compliance from the project's outset, your organisation avoids significant fines and builds stakeholder trust, which is a valuable intangible asset.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
A top-tier consultant acts as a strategic business partner, not just a technical advisor. They possess deep industry knowledge relevant to your sector, understand the German regulatory landscape intimately, and focus on enabling business objectives securely.
When is the optimal time to engage a consultant?
The earlier, the better. For maximum impact, a cyber security consultant should be engaged during the strategic planning or initial conceptual phase of a project.
Early involvement ensures that security and compliance are integrated into the project's architecture, rather than being addressed as costly afterthoughts. This "security by design" approach fundamentally de-risks the entire initiative. To understand what this looks like in practice, you can learn more about deploying secure, self-hosted AI in our guide on building a cost-efficient LLM cluster.
At Reruption, we serve as your Co-Preneurs for the AI era, assuming shared accountability for transforming your ambitious ideas into secure, market-ready innovations. Discover how our AI Security & Compliance services can de-risk your most critical projects at https://www.reruption.com.