In the current business landscape, strategic IT Security Beratung has evolved from a traditional cost centre into a critical driver of enterprise value. It is now an essential strategic function for the secure deployment of emergent AI technologies. Effective IT security advisory acts as a strategic partner, transforming potential cyber risks into opportunities for growth and securing a competitive advantage in a dynamic global market.
Why Traditional Security Consulting Is Failing in the AI Era
For executive leadership in Germany's leading enterprises, the strategic context for IT security has fundamentally shifted. The rapid integration of artificial intelligence, compounded by increasingly sophisticated cyber threats and stringent regulatory frameworks such as NIS 2, has rendered conventional IT security consulting models obsolete. Yesterday's reactive, project-based security engagements are insufficient for the dynamic, persistent challenges of today's digital ecosystem.

The outdated paradigm typically treats security as a downstream compliance activity, executed long after core innovation has occurred. This approach creates operational friction, impedes time-to-market, and leaves significant vulnerabilities exposed—a critical deficiency in accelerated AI development cycles. As AI solutions are increasingly deployed on cloud infrastructure, the capability to understand and proactively mitigating cloud computing security risks is an area where traditional consultants frequently lack the required depth.
The Shift from Cost Centre to Strategic Enabler
Modern enterprises require a strategic partner, not merely another technical vendor. A contemporary IT Security Beratung partner must comprehend the P&L implications of security decisions and integrate security principles into the fabric of innovation from its inception. This proactive approach transforms security from a reactive expenditure into a powerful business enabler that underpins secure, sustainable growth.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
The objective is no longer confined to threat mitigation. It is about constructing a resilient foundation that provides the confidence to innovate at pace. A modern security partner functions as a co-pilot, navigating complexity to ensure AI initiatives are not only pioneering but also secure and compliant.
This strategic alignment is the catalyst that transforms ambitious concepts into market-ready realities.
Addressing the Critical Skills Gap in Germany
This strategic challenge is exacerbated by a pronounced talent deficit within the German market. The IT security services industry has expanded to a market size of €4.5 billion, a figure indicative of the urgent demand for specialised expertise.
With 109,000 open positions for IT specialists and a staggering 85% of companies reporting a significant skills bottleneck, internal teams are operating at maximum capacity. This gap inhibits innovation and necessitates reliance on external experts for high-stakes IT Security Beratung. This market reality positions expert consulting not as an optional expense, but as a strategic imperative for maintaining competitiveness.
The Four Pillars of a Modern IT Security Partnership
For any leader driving a digital transformation agenda, a modern IT security partner must deliver more than tactical system remediation. They must provide a strategic framework built upon foundational pillars that align directly with core business objectives. An effective IT Security Beratung delivers tangible outcomes, ensuring security functions as an enabler of innovation, not an impediment.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.

This partnership model is founded on four interdependent pillars. They function in concert to build an enterprise that is both resilient and prepared for future challenges. Let's examine how each pillar safeguards the organization while enhancing its competitive position.
Pillar 1: Strategic Risk Management
Fundamentally, security is the practice of managing risk to protect enterprise value and P&L. Strategic risk management translates abstract cyber threats into quantifiable business impacts, such as potential revenue loss, supply chain disruption, or reputational damage. This is a continuous, iterative process, not a singular assessment.
The process begins by identifying high-value corporate assets, including proprietary AI models, sensitive customer data, or critical operational technology. Subsequently, the specific threats facing these assets are analyzed. The result is a clear, prioritized roadmap for security investment, ensuring capital is allocated to areas with the highest impact on protecting business value.
A mature risk management programme provides a definitive answer to the board's critical question: "Where are our most significant vulnerabilities, and what is the financial exposure if we fail to act?" It elevates the security discussion from technical jargon to a strategic business imperative.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
Pillar 2: Technical Vulnerability Analysis
While strategy provides direction, technical analysis establishes ground truth. This pillar involves the rigorous testing of systems, applications, and infrastructure to identify exploitable weaknesses before malicious actors do. These are, in effect, controlled, ethical penetration tests of your digital estate.
These are not perfunctory compliance exercises; they are essential for operational integrity. Key activities include:
- Penetration Testing: Simulating a real-world cyberattack to validate the effectiveness of existing defenses.
- Vulnerability Scanning: Employing automated tools to continuously identify known security flaws and outdated software.
- Code Reviews: Scrutinizing the source code of applications, particularly new AI tools, to eliminate security defects early in the development lifecycle.
Proactively identifying and remediating these weaknesses reduces the organization's attack surface, making it a less attractive target for cybercriminals. This constitutes the core of any credible information security consulting engagement.
Pillar 3: Incident Response and Business Continuity
Even the most robustly defended organizations must prepare for the eventuality of a security breach. A well-rehearsed incident response plan is the operational playbook for crisis management. Its purpose is to minimize damage and restore business operations as swiftly as possible. The ultimate objective is ensuring business continuity.
This pillar emphasizes preparedness. It requires that roles, responsibilities, and communication protocols are clearly defined before an incident occurs. A robust plan enables the team to detect, contain, and neutralize threats methodically, preventing the chaotic decision-making that exacerbates a crisis. Regular drills and simulations are vital to maintaining the plan's efficacy and the team's readiness.
Pillar 4: Compliance and Governance
Compliance frameworks such as TISAX and ISO 27001 are the currency of trust, particularly in demanding sectors like automotive and manufacturing. This is not about administrative overhead; it is a verifiable commitment to security and data protection. Adherence to these standards demonstrates to clients, partners, and regulators that the organization operates with integrity.
A strategic partner guides the organization through the entire certification journey, from initial gap analysis to final audit. This process not only strengthens defenses but also builds a significant competitive advantage, opening access to new business with major clients who mandate the highest security standards.
Turning Compliance Frameworks into a Competitive Advantage
For many executive boards, compliance is perceived as a necessary but non-value-adding activity. In highly regulated industries such as automotive and manufacturing, it is often viewed as the cost of market participation. However, viewing frameworks like TISAX or ISO 27001 merely as checklists represents a significant missed strategic opportunity. A modern IT security consulting approach reframes these standards not as burdens, but as blueprints for a more resilient and trustworthy enterprise.
These frameworks are more than technical specifications; they are a public declaration of an organization's commitment to operational excellence. Certification signals to clients—particularly large enterprises—that you operate at a superior standard of security. It establishes a moat of trust around your business that is difficult for competitors to replicate.
In a landscape of persistent threats, this trust is paramount. The German cybersecurity market has already reached a valuation of approximately USD 12 billion, with consulting services at the core of this growth. Projections indicate the market will reach USD 31.15 billion by 2035, a testament to mounting regulatory pressure and the increasing complexity of cyber threats. Further analysis of the German cybersecurity market is available from Ken Research.
From Blueprint to Fortress: The Certification Journey
Achieving certification for standards like TISAX or ISO 27001 is a structured project that fundamentally transforms an organization's security posture. It is a methodical process that converts abstract principles into concrete, operational defenses. A valuable partner does not simply provide a list of requirements; they engage directly with your team to guide the implementation.
The process is typically structured in three phases:
- Initial Gap Analysis: A comprehensive diagnostic assessment of your current controls, processes, and documentation against the standard's specific requirements. The deliverable is a clear, prioritized roadmap detailing necessary remediation actions.
- Strategic Implementation: This phase involves executing the roadmap. Gaps are closed through the development of new security policies, implementation of technical controls, and—critically—employee training. This is a collaborative effort to embed best practices into daily operations.
- Audit Preparation and Support: In the final phase, your partner assists with organizing all necessary documentation, conducts pre-audit assessments to identify any remaining issues, and provides support during the formal audit to ensure a successful outcome.
Beyond the Certificate: The Real Business Impact
Certification is not the endpoint; it is the validation of a new operational baseline. The true return on investment stems from the discipline and resilience cultivated throughout the process. For example, a robust ISO 27001 implementation fundamentally strengthens risk management capabilities, making the entire organization better prepared for future challenges. The integration of these concepts is further detailed in our guide on integrating risk management and compliance.
The certificate is tangible proof of the fortress you have built. The enduring competitive advantage is derived from enhanced client trust, more stable operations, and the confidence to pursue ambitious digital initiatives without undue risk.
This process systematically de-risks the entire operation. It hardens the company against attacks, refines internal processes, and aligns the entire organization around a unified security strategy. When compliance is approached proactively rather than reactively, it becomes a powerful engine for secure and sustainable business growth.
How to Secure Your AI and Machine Learning Innovations
Artificial intelligence introduces a new class of security risks that legacy systems are ill-equipped to address. For leaders of innovation, this new frontier requires a fundamentally different security playbook. Applying outdated security protocols to AI and Machine Learning projects is not only inefficient; it is strategically perilous.
The threats themselves are distinct. The focus expands beyond network breaches to include risks such as data poisoning, where an adversary subtly corrupts training data, causing the AI model to produce flawed and costly outputs. Another threat is model inversion, where an attacker can reverse-engineer an AI to expose the sensitive, proprietary data on which it was trained. These are not mere IT issues; they are significant business risks that can erode trust, compromise intellectual property, and negatively impact financial performance.
Integrating Security into the MLOps Lifecycle
To effectively counter these novel threats, security must be an integral component of the entire Machine Learning Operations (MLOps) lifecycle, not a final checkpoint. It must be engineered into the process from the outset.
This requires addressing critical security questions at each stage:
- Data Ingestion: How do we verify the integrity of our training data to prevent data poisoning attacks?
- Model Training: What measures are in place to protect the model from theft or manipulation during its development?
- Deployment: How do we secure the APIs that expose the model's predictive capabilities?
- Monitoring: What systems are in place to detect anomalous behavior that could indicate an ongoing attack?
An expert IT Security Beratung partner helps operationalize these questions, transforming them from abstract concerns into automated checks and balances within your development pipeline.
De-Risking Innovation with Practical Examples
Consider a Natural Language Processing (NLP) chatbot designed for customer service. Without adequate security, an attacker could manipulate its inputs to elicit inappropriate or damaging responses, severely harming brand reputation. A specialist consultant would implement input validation and adversarial testing to harden the chatbot against such manipulation.
Another example is a predictive maintenance model for a manufacturing facility. A compromised model could fail to predict critical equipment failures or trigger false alarms, both leading to significant operational downtime and financial loss. Securing this model involves implementing robust access controls and continuous monitoring to ensure the integrity of its predictions. For Large Language Models, robust LLM observability, monitoring, and debugging are non-negotiable for identifying and neutralizing these threats.
The Strategic Role of IT Security Beratung in AI
Navigating this complex risk landscape requires a specific skillset that combines deep cybersecurity expertise with a practical understanding of AI development. This is where specialized IT Security Beratung becomes a critical catalyst for innovation.
A true strategic partner does not simply enumerate risks; they provide the frameworks and tools to manage them effectively. They de-risk your AI projects, empowering your organization to pursue ambitious goals without assuming unacceptable levels of risk.
The infographic below illustrates a structured process for achieving compliance with standards like TISAX or ISO 27001. These frameworks provide a solid foundation for securing all IT systems, including your AI infrastructure.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.
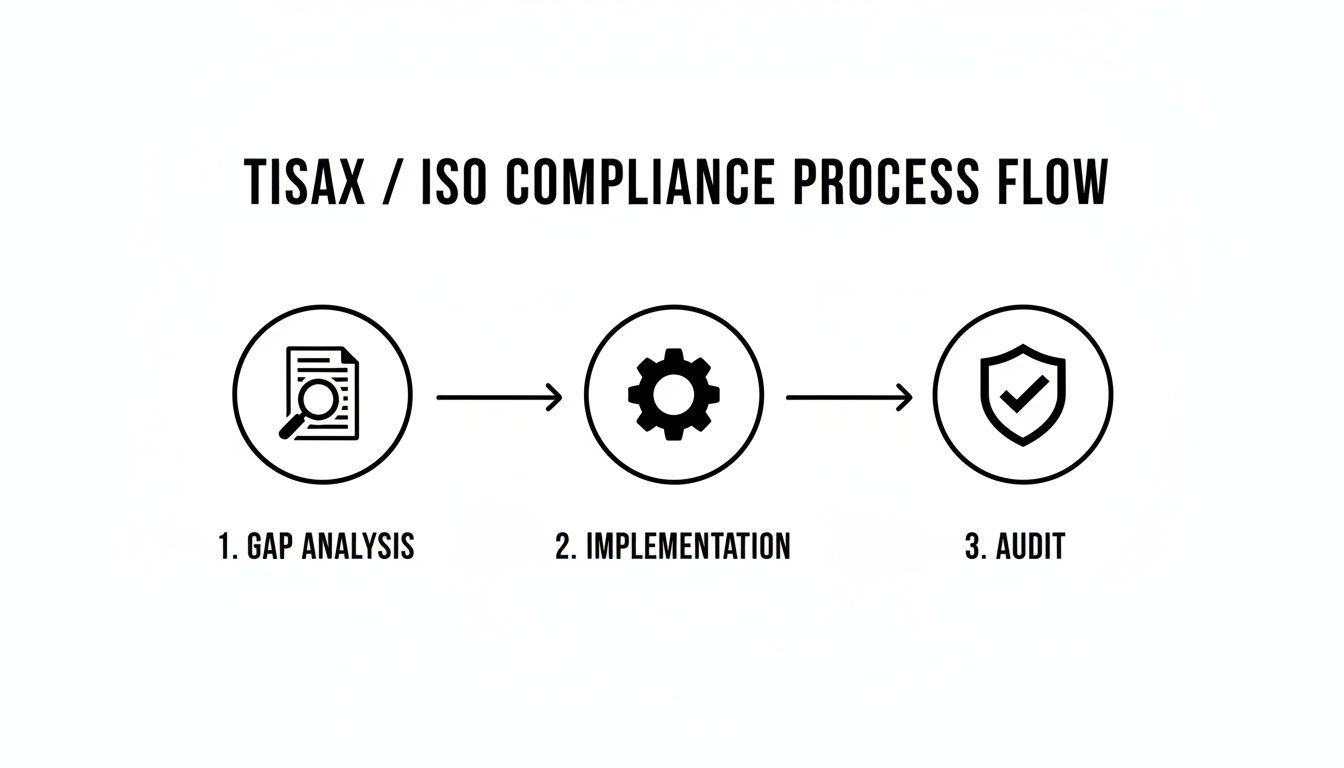
This methodical approach ensures that security becomes a systematic component of your operations. By treating AI security as a core business function from inception, you can unlock its immense potential without exposing your organization to commensurate threats. For a more detailed exploration, see our guide on creating audit-proof AI systems for the enterprise.
A C-Level Checklist for Selecting Your IT Security Partner
Selecting an IT security partner is a strategic decision with significant long-term implications. The right firm is not a vendor; it is an enabler of secure, AI-driven growth. To identify such a partner, executives must look beyond standard technical certifications and assess for deep business alignment.
This requires a rigorous evaluation process that focuses on pointed questions designed to differentiate tactical suppliers from true strategic allies. The criteria should center on proven expertise, a model of shared accountability, and a track record of delivering measurable business outcomes.
Assessing Strategic and Technical Depth
Your ideal partner must possess a unique combination of deep cybersecurity knowledge and a nuanced understanding of AI's specific vulnerabilities. Many firms excel in one domain but falter at their intersection—precisely where the most significant business risks now reside. A top-tier IT Security Beratung provider must be fluent in the language of both the CISO and the Head of Innovation.
Want to Accelerate Your Innovation?
Our team of experts can help you turn ideas into production-ready solutions.
During the vetting process, consider these questions:
- Beyond Certifications: "Provide a case study where you secured a complex AI or machine learning deployment. What were the specific threats mitigated, and what was the quantifiable business outcome?"
- Integrated Expertise: "Describe the collaborative workflow between your cybersecurity and AI teams. Is this collaboration standard for relevant projects, or are they functionally siloed?"
- Proactive Threat Modelling: "Explain your methodology for identifying threats to a new AI system before it is developed. How do you model risks like data poisoning or model inversion in terms of business impact?"
The answers should demonstrate a history of solving forward-looking security challenges, not just reacting to past incidents.
Evaluating the Partnership and Accountability Model
A traditional, project-based relationship is inadequate for the relentless pace of AI innovation. You require a partner who is genuinely invested in your success and shares accountability for the outcomes. This involves a shift from a model based on billable hours to one centered on shared objectives and tangible results.
A true partner adopts a "co-preneurial" mindset. They should be as focused on the P&L impact of your AI initiatives as you are, because their success is intrinsically linked to yours.
This redefines the client-consultant dynamic. The focus shifts from completing a statement of work to achieving a strategic business objective together. To assess this alignment, inquire about their engagement model and performance metrics. For further insight into this modern partnership, you can explore the core principles of cyber security consultancy and its role in driving strategic growth.
Focusing on Tangible Business Outcomes
Ultimately, the value of any IT Security Beratung engagement is measured by its contribution to the bottom line. This includes preventing significant financial losses from breaches, enabling new revenue streams through secure innovation, and building market trust via robust compliance. A strategic partner must be able to articulate their value in these precise terms.
Key questions to assess their focus on ROI include:
- Measuring Success: "Beyond technical metrics, what specific KPIs do you use to measure the success of a security engagement?"
- Business Enablement: "Provide an example where your security guidance directly enabled a client to launch a new product or enter a new market faster or more securely."
- Board-Level Communication: "How do you translate complex technical findings into a clear narrative of business risk and ROI for an executive board?"
Utilizing this checklist will help you penetrate the standard procurement rhetoric and identify a partner genuinely equipped to secure your future innovations and contribute to your competitive success.
Vendor Selection Checklist for Strategic IT Security Partnership
For C-level executives, selecting an IT security partner in the age of AI is a high-stakes decision. The table below outlines key criteria to help you distinguish a tactical vendor from a strategic co-preneur who will share accountability for your business outcomes.
| Evaluation Criterion | Key Questions to Ask | Why It Matters for ROI |
|---|---|---|
| Proven AI/ML Expertise | "Show me a real-world case study of securing an AI model like ours. What specific vulnerabilities did you find and fix?" | Reduces risk of catastrophic failures (e.g., model theft, data poisoning) that directly impact revenue and brand trust. |
| Co-Preneurial Model | "How is your success measured? Are your incentives tied to our business outcomes, or just billable hours?" | Ensures the partner is motivated to find efficient, effective solutions that boost your P&L, not just run up a bill. |
| Speed & Prototyping | "How fast can you build a security prototype or run a proof-of-concept for a new AI initiative?" | Enables faster time-to-market for new, secure products, directly accelerating revenue generation. |
| Business-Focused Reporting | "Can you provide an example of a report you've prepared for a board of directors? How do you quantify risk in financial terms?" | Translates technical issues into clear business language, enabling better strategic decisions and investment justification. |
| Integrated Skill Sets | "How do your security experts, data scientists, and business strategists collaborate on a typical project?" | Avoids siloed thinking that misses critical, cross-functional threats, preventing costly blind spots in your security posture. |
| Proactive Threat Hunting | "What's your methodology for anticipating threats to AI systems that don't even exist yet?" | Gets ahead of emerging threats, preventing future breaches and avoiding the massive costs of reactive clean-up and reputational damage. |
Selecting the right partner is less about finding a supplier and more about recruiting an ally. A firm that can confidently answer these questions is one that understands security not as a cost centre, but as a fundamental driver of competitive advantage and sustainable growth.
The Co-Preneur Model: Shared Success and Real Accountability
The traditional consulting model is fundamentally misaligned with the demands of modern business. It is often too slow, disconnected from strategic objectives, and lacks genuine accountability. For the high-stakes, fast-paced environment of AI innovation, a transactional relationship that culminates in a slide deck is insufficient. A new model built for speed, agility, and shared success is required.
The Co-Preneur model redefines the client-consultant dynamic into a true partnership. In this framework, your security partner is deeply invested in the commercial success of your AI initiatives, not merely in the delivery of services. Their success is synonymous with your success.
P&L Accountability in Practice
In practical terms, this means your IT security beratung partner shares P&L accountability. They function not as external advisors, but as an integrated, entrepreneurial component of your team. Their focus shifts from identifying problems to actively co-creating secure, market-ready solutions that contribute to your top and bottom lines.
This model is predicated on two core principles: velocity and intelligent risk management.
- Velocity: The objective is to progress from concept to a secure prototype in weeks, not months. This speed enables rapid validation of business hypotheses and accelerates time-to-market.
- Methodical De-risking: Security is integrated into the innovation process from its inception, not applied retroactively. This ensures that speed does not compromise resilience or compliance.
This hands-on approach is increasingly critical in the German market. The Security Services segment experienced 13.8% annual growth in 2023, driven by intense demand for IT security. Concurrently, a severe labor shortage—with 85% of firms reporting difficulty in hiring IT specialists—is compelling companies to rely more heavily on expert advisory services. The underlying data can be explored in this Statista report.
An Entrepreneurial Extension of Your Team
A Co-Preneur partner adopts an ownership mentality. They are as concerned with a project's market viability and profitability as they are with its security posture. This alignment eliminates the traditional friction between innovation teams seeking to accelerate and security teams perceived as applying brakes.
When your security partner is accountable for the same business outcomes as you are, the entire conversation changes. Security stops being a gatekeeper and becomes a strategic enabler for launching ambitious, resilient, and profitable AI initiatives.
Ultimately, this model is about converting bold ideas into tangible, secure innovations that create measurable value. It ensures your IT security partner is not just another vendor but a committed ally, helping you navigate the complexities of the AI era and build a more prosperous future for your organization.
A Few Common Questions About IT Security Beratung
For business leaders in Germany considering an engagement with an IT security partner, several questions naturally arise. The following provides direct, C-suite-oriented answers, focusing on the practical application and business value of such a partnership.
The objective is to demystify the process and illustrate the tangible contributions a true partner can make to your financial performance.
How Do You Actually Measure the ROI of Security Consulting?
Measuring the return on investment for security consulting extends beyond technical metrics like patched vulnerabilities. For executives, the true value lies in business enablement and risk reduction, which can be quantified in several key areas.
First, consider cost avoidance. A robust security engagement directly reduces the financial exposure associated with a data breach, including regulatory fines, operational downtime, and brand damage. The ROI is the catastrophic event that was prevented.
Second, focus on revenue enablement. A strong security posture, particularly when validated by a certification like TISAX, is a business asset. It unlocks access to new markets and major clients with stringent security requirements. The ROI here is the net new business that becomes attainable.
Finally, value can be measured in operational efficiency. An effective partner streamlines security processes, rather than adding complexity. This liberates internal teams from reactive "fire-fighting," allowing them to focus on core business objectives and innovation.
What's a Realistic Timeline for TISAX Certification?
Achieving a TISAX (Trusted Information Security Assessment Exchange) label is a structured journey. The specific timeline depends on the organization's initial maturity level, but for a larger enterprise, the process can be divided into distinct phases.
Looking for AI Expertise?
Get in touch to explore how AI can transform your business.
- Phase 1: Gap Analysis & Scoping (4-6 weeks): This initial phase involves a detailed assessment of your current security controls against the TISAX requirements to identify all deficiencies. The output is a clear, prioritized roadmap for remediation.
- Phase 2: Remediation & Implementation (3-6 months): This is the execution phase. We collaborate with your team to close all identified gaps, which may involve updating policies, implementing new technical controls, and conducting employee training.
- Phase 3: Audit Preparation & Execution (4-8 weeks): In the final stage, we assist in preparing all necessary documentation, conduct internal pre-audits to ensure readiness, and support your team during the official TISAX assessment.
While timelines can vary, a well-managed project for a large enterprise typically requires six to nine months from initiation to certification.
How Does a Partner Fit in with Our Internal IT Team?
A common concern is that an external consultant will create friction with the in-house IT team. This reflects an outdated model of consulting. A modern IT security beratung partner integrates seamlessly as an extension of your team, aligned around a common objective.
The objective is collaboration, not replacement. A strategic partner acts as a force multiplier, bringing specialised expertise in areas like AI security or specific compliance frameworks that your internal team may not possess.
This collaborative model succeeds through constant communication and clearly defined roles from the outset. The consulting partner provides strategic guidance and handles complex implementations while actively mentoring your team. This facilitates knowledge transfer, strengthening your organization's internal capabilities for the long term.
At Reruption GmbH, we don't just consult; we operate as Co-Preneurs. We share P&L accountability to turn your innovative ideas into secure, market-ready realities. Discover how our unique approach to IT security drives growth by visiting us at https://www.reruption.com.
Ready to Build Your AI Project?
Let's discuss how we can help you ship your AI project in weeks instead of months.